Self-study for eJPT (eLearnSecurity Junior Penetration Tester) from eLearnSecurity. Pass your exam on the first attempt If you can’t afford the price of INE training follow these topics.
Before the Exam
Before starting the exam I recommend you to sleep well and after that have a great meal.
Remember to Take a shower before the Exam and clean your desk.
Go to the supermarket and buy some food and drinks for yourself and if you have a pet like me, buy food for it and clean its toilet.
If you have anything in your mind to do, do it before starting the exam.
Just clean your head!
Table of Contents
Reload the machine…
Just turn it off while you are Hacking! You are being prepared for the real world 😛
Before starting, the exam verifies if you have backups of all virtual machines you need or tools, documentation, and binaries.
If you can afford a dedicated external disk for all your security/certification stuff, do it!
eJPT Certification
After you execute all procedures and your Lab is prepared click the Start button and enjoy your journey. You can do it!
Methodologies
Usually in certification labs or executing a penetration test on a client we have defined in our scope a subnet with a specified range of IPs.
Before start scanning the network I usually execute some commands on my machine to verify what interface is associated with the VPN to verify my IP and verify my ARP table.
Networks can filter types of traffic or traffic to specific port numbers. Pay attention if you trying to get a reverse shell on a random port number, that port could be blocked.
What if the Network is blocking some types of traffic?
As I said networks can filter types of traffic like TCP/UDP/SCTP/ICMP or even IP, yes IP!
UDP traffic can be blocked only for a specific host and allowed for others inside the same subnet.
Or can be blocked on all subnets.
In these cases, we need to test the network for each host we’ve found.
Web Tools
| Tools | Description | URL |
| RevShells | https://www.revshells.com/ | |
| CyberChef | https://gchq.github.io/CyberChef/ | |
| SecLists | https://github.com/danielmiessler/SecLists | |
| GTFOBins | https://gtfobins.github.io/ | |
| Crackstation | https://crackstation.net/ | |
| LOLBAS | https://lolbas-project.github.io/ | |
Information Gathering
As we know it all starts with information gathering, we need to collect much data as we can from our network environment. In a lab environment, we don’t need to collect public information (OSINT) but we need all information related to our machines, like hostnames, ports, services/versions, usernames, and domains.
Check the next chapter footprinting & scanning.
Read some articles about how to Map the Network using OSINT
Footprinting & Scanning
It’s time to start mapping all hosts and services, we can use Nmap to get all the information we need! Start by scanning the subnet ranges to detect live hosts and then scan each host to detect open ports and what services are running on them.
Not all network banners expose the service version if some services don’t expose the versions try to find them, and some exploits only work on specific versions, using specific CPU architectures.
Mapping the Network
Scanning each subnet using the Ping scan is faster to detecting live hosts, but some of them may not respond to ICMP requests in that case use a Syn scan.
OS fingerprinting and Port Scanning
After detecting live hosts on the network it’s time to enumerate what operating system is running on it, we can do it using the ping command but at this point, Nmap probably already detects it for you, if not use the parameter -O, and scan again.
| Tool | Description | Article |
| Nmap | ||
| rustscan |
In this category, it’s all about your knowledge, if you can manually find vulnerabilities great if not use a scanner.
Vulnerability scanners nowadays are easy to manage and detect a lot of vulnerabilities, there are no restrictions on what tools you can use on eJPT.
Always try to find a vulnerability by digging manually but if you can’t find it and that is normal we are learning! use a Nessus or OpenVAS they will help you find some entry points.
You have all the information you need on my blog, check here:
| Tool | Description | Article |
| Nessus | ||
| OpenVAS | ||
| Nikto |
Junior Penetration Tester – Web Attacks
Web applications can be tricky you must be comfortable with some basic techniques used to attack the server side and client side, I highly recommend you start learning all the necessary topics on Portswigger Web Security Academy, they have all you need to master this topic, and all for FREE!
Web Enumeration
Enumerate what?
Before everything learns HTTP, it’s all about how HTTP works!
After scanning the host you found port 80 open, you need to understand what service is running there and what version, if find an exploit to get a reverse shell amazing you are in!
But what if you don’t find anything?
You need to start enumerating all information related to the web server and web application running.
Web servers have specific files for configurations that can be exposed to the public if you find one that can help get a way in.
And Web applications?
Web applications can be static and dynamic, on static pages you enume
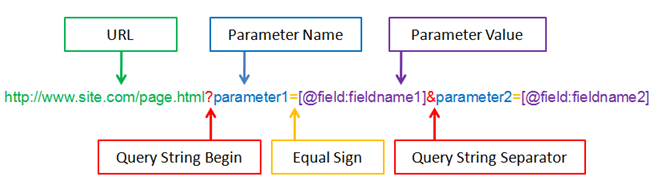
Web Servers
You should be familiar with some web servers and how to attack them, Apache is one of the most used web servers and it has a lot of well-known vulnerabilities. you should be able to enumerate the web server detect the Apache version and find an exploit online.
Keep calm, I will help you find them in fact I compile a list for you.
Another service you can find is the application server TomCat, you can read my article about to attack a TomCat service.
Wait and the Nginx?
If you find it, probably the vulnerability is in the application or how it communicates with other internal services using localhost.
But! Always verify the Nginx version and search exploits available.
searchsploit nginx| Tool | Description | Article |
| gobuster | ||
| ffuf | ||
| feroxbuster | ||
Web Applications / CMS
On eJPT the most common web CMS is WordPress, you should be familiar with the platform and enumerate users, plugins, and themes.
After you have access you need to find a way to upload a PHP shell to control the web server or better upload a reverse shell, Metasploit can help with all these steps or do it manually.
| Tools | Description | Article |
| wpscan | Attack WordPress Website | |
Network Attacks
Understand different scan types and how to brute-force network services,
Brute Force Services
- Learn How to Attack FTP Service vsftpd 2.3.4
- How to Brute Force Database Services
- How to Brute Force Email Services
- How to Brute force FTP Services
- How to Brute Force Remote Access Protocols
| Protocol | Ports | Article |
| FTP | 21 | |
| TELNET | 23 | |
| SSH | 22 | |
| SMB | 445, 139 | |
| RDP | 3389 | |
| NetBIOS | 135,137,138 | |
| RPC |
Databases
eJPT – System Attacks
Crack Passwords
| Tool | Description | Article |
| john the ripper | ||
| hashcat | ||
| unshadow | ||
Metasploit
sysinfo, ifconfig, route, getuid
getsystem (privesc)
bypassuac
download x /root/
upload x C:\\Windows
shell
use post/windows/gather/hashdumpLinux
Windows
eJPT Exploits
run autoroute -s 192.168.1.0/24use auxiliary/scanner/portscan/tcp
set PORTS <ports>
set RHOSTS 192.168.1.95
runChisel Reverse Proxy: Pivoting Networks
TryHackMe Rooms
| Room | Description | Walkthrough |
| Wreath | ||
| Kenobi | ||
Playlist: eJPT Certification Free Study


Comments