Pivoting with SSH can be very useful will performing a pentest assessment inside a big network. Many people confuse Pivoting with port forwarding but they are different techniques and they can be used together to achieve the final goal.
Using SSH to pivot inside a network is very easy you just need to think how a socket works. One socket can be created with two end points and that establish a tunnel. Using the SSH protocol this tunnel can be divided in different sessions.
Each session can be used to access different networks or remote services using remote port forwarding.
Pivoting vs Port Forwarding
Pivoting is the process of routing our traffic throught other machine to access other sub networks or resources. (Socks5)
Port Forwarding is more limited we only deal with ports and we can map them locally or remotelly. (Socks4)
SSH Pivoting Lab 1 – First Tunnel
After you have access to the webserver machine with IP 148.148.148.5 and you have logged in with an SSH account, its time to start building our sockets. [adinserter block=”4″]
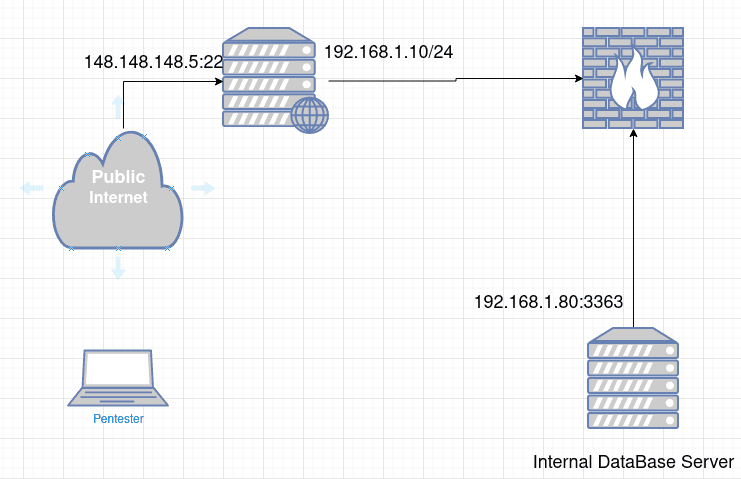
Using the next network diagram as an example. We have one webserver with two interfaces, one interface is exposed on the internet (148.148.148.5) the other have access to the internal network (192.168.1.10/24).
After you has a pentester gain access to the webserver machine and you check the machine have an other interface into a different network. What WE think? Let’s scan that damn network and a new session of enumeration begins.
Right?
But if the Webserver machine dont have nmap? masscan? gobuster? dirb? curl? or another tool you will need?
How can we use this tools on our machine and scan the network 192.168.1.0/24?
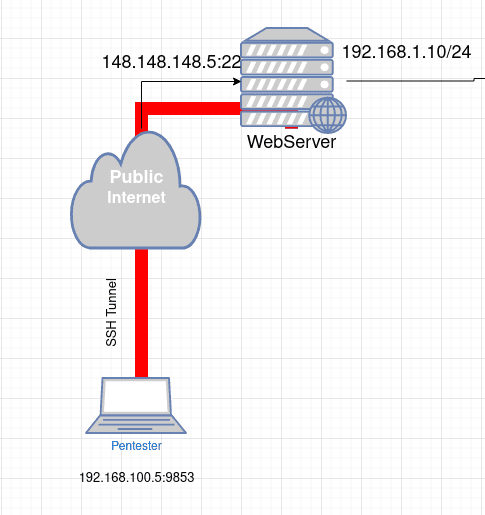
To make a normal SSH connection you probably use this command:
ssh [email protected]Using the above command you establish a simple SSH connection to the WebServer.
You have a source IP and a source port and a remote IP and remote port.
The next images represent a basic SSH connection mapping all socket end points.

Easy right?
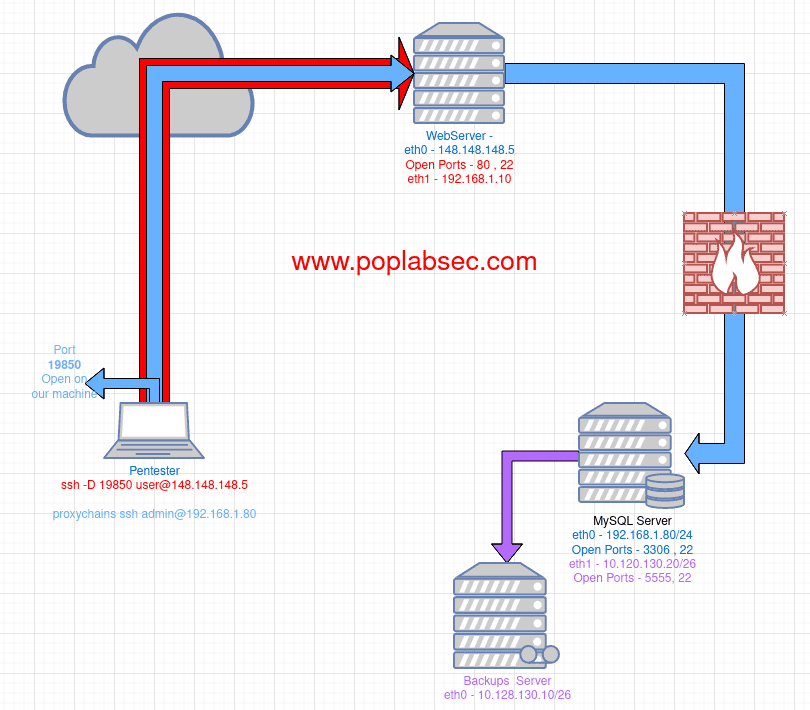
On the next example we will split that tunnel and inject our traffic through it and access the internal database server with IP 192.168.1.80.
[adinserter block=”4″]
SSH Pivoting Lab 2 – Second Tunnel
At this point we all ready have the connection to WebServer with IP 148.148.148.5 but if we want to access the internal network is necessary to use a SSH functionality like SSH Dynamic Port Forward.
This SSH functionality uses Socks5 protocol to proxy all our traffic through the base SSH tunnel (red)
[adinserter block=”4″]
ssh -D 19850 [email protected]proxychains ssh [email protected]


Comments