CrackMapExec (also known as CME) is a post-exploitation program that assists in automating the security assessment of large Active Directory infrastructures.
CME was designed with stealth in mind, exploiting built-in Active Directory functionality to achieve its functionality and evading most endpoint protection/IDS/IPS technologies.
Table of Contents
Install CrackMapExec
If you are using Kali you can install it from Kali repos but I recommend you install it from git source.
apt install crackmapexecIn this article I will install it on a Linux machine but if you need you can use it on Windows or using docker.
First, let’s install some dependencies
apt-get install -y libssl-dev libkrb5-dev libffi-dev python-dev build-essentialgit clone https://github.com/Porchetta-Industries/CrackMapExeccd CrackMapExecpoetry installpoetry run crackmapexecConfigure CrackMapExec
┌──(rfs㉿local-c2)-[~]
└─$ cd ~/.cmeChange CrackMapExec Certificate
┌──(rfs㉿local-c2)-[~]
└─$ vi ~/.cme/cme.conf┌──(rfs㉿local-c2)-[~]
└─$ openssl req -newkey rsa:2048 -new -nodes -x509 -days 3650 -keyout key.pem -out cert.pemTarget Definition
crackmapexec <protocol> ms.evilcorp.org
crackmapexec <protocol> 192.168.1.0 192.168.0.2
crackmapexec <protocol> 192.168.1.0/24
crackmapexec <protocol> 192.168.1.0-28 10.0.0.1-67
crackmapexec <protocol> ~/targets.txtCME Supported Protocols
SMB
MSSQL
LDAP
SSH
RDP
WINRMSamba Protocol
We will start scanning a network as an example and then a specific host on the network
crackmapexec smb 192.168.1.0/24crackmapexec smb 192.168.1.91Search Text Files
crackmapexec smb 192.168.1.15 -u 'Administrator' -p 'poplab!sec' --spider C\$ --pattern txtCME SMB Modules
| SMB Module | Description |
|---|---|
| ZeroLogon | Module to check if the DC is vulnerable to Zerologon aka CVE-2020-1472 |
| Petitpotam | Module to check if the DC is vulnerable to PetitPotam, credit to @topotam |
| ms17-010 | MS17-010, /!\ not tested oustide home lab |
| dfscoerce | Module to check if the DC is vulnerable to DFSCocerc, credit to @filip_dragovic/@Wh04m1001 and @topotam |
| nopac | Check if the DC is vulnerable to CVE-2021-42278 and CVE-2021-42287 to impersonate DA from standard domain user |
| shadowcoerce | Module to check if the target is vulnerable to ShadowCoerce, credit to @Shutdown and @topotam |
| Module | Description |
|---|---|
| gpp_autologin | Searches the domain controller for registry.xml to find autologon information and returns the username and password. |
| gpp_password | Retrieves the plaintext password and other information for accounts pushed through Group Policy Preferences. |
| handlekatz | Get lsass dump using handlekatz64 and parse the result with pypykatz |
| hash_spider | Dump lsass recursively from a given hash using BH to find local admins |
| keepass_discover | Search for KeePass-related files and process. |
| keepass_trigger | Set up a malicious KeePass trigger to export the database in cleartext. |
| lsassy | Dump lsass and parse the result remotely with lsassy |
| masky | Remotely dump domain user credentials via an ADCS and a KDC |
| teams_localdb | Retrieves the cleartext ssoauthcookie from the local Microsoft Teams database, if teams is open we kill all Teams process |
| wdigest | Creates/Deletes the ‘UseLogonCredential’ registry key enabling WDigest cred dumping on Windows >= 8.1 |
| wireless | Get key of all wireless interfaces |
MSSQL Protocol
CrackMapExec Modules to attack MsSQL Service.
MsSQL Modules
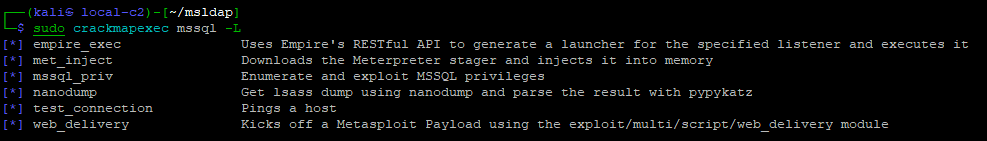
| Module | Description |
|---|---|
| empire_exec | Uses Empire’s RESTful API to generate a launcher for the specified listener and executes it |
| met_inject | Downloads the Meterpreter stager and injects it into memory |
| mssql_priv | Enumerate and exploit MSSQL privileges |
| nanodump | Get lsass dump using nanodump and parse the result with pypykatz |
| test_connection | Pings a host |
| web_delivery | Kicks off a Metasploit Payload using the exploit/multi/script/web_delivery module |
Privilege Escalation
Privilege escalation holds a significant role in security assessments as it enables testers to enhance their level of access within a system. By gaining additional privileges, such as accessing more users, hosts, and resources, security assessments can advance closer to achieving their objectives.
This phase is crucial as it helps in identifying vulnerabilities and weaknesses that could be exploited by malicious actors.
References
https://crackmapexec.popdocs.net/
What is CrackMapExec?
CrackMapExec (CME) is a free and open-source tool used for network enumeration and penetration testing, particularly on Windows networks. It allows pentesters to gather information about hosts, services, users, and groups within a network.
Is CrackMapExec legal to use?
Using CrackMapExec is legal only with explicit permission from the network owner. Using it on unauthorized networks is illegal and can have serious legal consequences.
What are the ethical considerations of using CrackMapExec?
CME is a powerful tool, and its use should adhere to ethical hacking principles. It should only be used in controlled environments with proper authorization and for legitimate security testing purposes.
Is CrackMapExec still maintained?
The original CrackMapExec project is no longer actively maintained. However, there are community-maintained forks available.


Comments