Welcome to our comprehensive guide on SMB Penetration Testing! In this video, we delve into the crucial steps to secure your network against potential threats.
Small and Medium-sized Businesses (SMBs) are often prime targets for cyberattacks, and understanding how to effectively conduct penetration testing is essential for safeguarding sensitive information.
Table of Contents
Introduction to Samba Protocol
Samba is used to share network resources between different Operating Systems it controls access to network shares, printer services, and interconnection with old protocols.
SMB (Samba) was defined as a standard to share folders between Windows and Linux it can act like a domain controller or connect to an Active directory as a client, so many features can’t be offered without vulnerabilities.
Since 1992 many versions have been released carrying tons of vulnerabilities with each one, next, I compile a table with each version to help us search CVEs.
Versions of Windows SMB
| Windows Version | SMB Version |
|---|---|
| Windows 95 | SMB 1.0 |
| Windows 98 | SMB 1.0 |
| Windows NT 4.0 | SMB 1.0 |
| Windows 2000 | SMB 1.0 |
| Windows XP | SMB 1.0 |
| Windows Server 2003 | SMB 1.0 |
| Windows Vista | SMB 2.0 |
| Windows Server 2008 | SMB 2.0 |
| Windows 7 | SMB 2.1 |
| Windows Server 2008 R2 | SMB 2.1 |
| Windows 8 | SMB 3.0 |
| Windows Server 2012 | SMB 3.0 |
| Windows 8.1 | SMB 3.0 |
| Windows Server 2012 R2 | SMB 3.0 |
| Windows 10 | SMB 3.0/3.1 |
| Windows Server 2016 | SMB 3.0/3.1 |
| Windows Server 2019 | SMB 3.0/3.1 |
Navigating the intricate details of network protocols might seem like an overwhelming task, but having basic knowledge of key elements like SMB Port Numbers can bring significant clarity.
SMB, which stands for Server Message Block, is a protocol utilized for sharing access to files, printers, and serial ports on a network.
This article aims to shed light on SMB Port Numbers, highlighting their crucial role in enabling systematic communication between devices interconnected within a network.
| SMB Version | Port Number | Protocol | Description |
|---|---|---|---|
| SMB 1.0 | 137/UDP | NetBIOS | Legacy version of SMB used in older Windows systems. Ports 137/UDP and 138/UDP are used for NetBIOS name resolution, and port 139/TCP is used for NetBIOS session communication. Considered less secure due to vulnerabilities and limitations. |
| SMB 2.0 | 445/TCP | TCP | Introduced in Windows Vista and Windows Server 2008. It improves file sharing and provides better performance. Uses port 445/TCP for direct host-to-host communication over TCP. |
| SMB 2.1 | 445/TCP | TCP | An enhancement of SMB 2.0, introduced in Windows 7 and Windows Server 2008 R2. Offers improved performance and security features. Uses port 445/TCP. |
| SMB 3.0 | 445/TCP | TCP | Introduced in Windows 8 and Windows Server 2012. Brings significant improvements, including better performance, security features, and support for larger file sizes. Uses port 445/TCP. |
| SMB 3.0/3.1 | 445/TCP | TCP | Continuation of SMB 3.0 with further enhancements. Introduced in Windows 8.1 and Windows Server 2012 R2. Supports features like SMB encryption and persistent handles. Uses port 445/TCP. |
Whether you’re IT professional or an aspiring tech enthusiast, understanding the role and relevance of SMB Port Numbers will give you an upper hand in maneuvering through network-related tasks or issues.
At this point, we know what Samba is and for what can be used, we need to enumerate remote shares, users/groups, disks, and respective privileges and passwords.
SMB RFCs
Here’s a table of common Samba RFCs (Request for Comments) with their corresponding RFC number and a brief description:
| RFC | Description |
|---|---|
| RFC 1001 | Defines the NetBIOS API and the NetBIOS Name Service used by Samba. |
| RFC 1002 | Defines the NetBIOS Session Service used by Samba to establish sessions. |
| RFC 1761 | Defines the Remote Procedure Call (RPC) protocol used by Samba. |
| RFC 2050 | Defines the Internet Registry (IR) used by Samba. |
| RFC 2307 | Defines the schema for representing POSIX accounts in LDAP directories. |
| RFC 2733 | Defines the SMB printing protocol used by Samba. |
| RFC 2849 | Defines the Lightweight Directory Access Protocol (LDAP) data interchange format. |
| RFC 3195 | Defines the Reliable Event Logging Protocol (RELP) used by Samba for logging. |
| RFC 3280 | Defines the Internet X.509 Public Key Infrastructure (PKIX) Certificate and Certificate Revocation List (CRL) Profile. |
| RFC 4120 | Defines the Kerberos authentication protocol used by Samba. |
These RFCs are important for understanding the protocols and standards used by Samba for networking and authentication, as well as for configuring and securing Samba servers.
Pentesting SMB
We scanned a remote machine and we noticed that port 445 is open and running SMB on it, the remote Operating System is a Linux machine with Ubuntu 18.04 on it!
At the moment we don’t know anything related to users, shares, passwords, permissions, or exploits.
SMB Enumeration
After we have detected SMB service running on port 445 or on another port we can start enumerating remote shares and understand their permissions (Read/Write/Execute) associated with each user/group on the system.
If we are lucky and find a remote share with RWX permissions without authentication containing documents or mapped to a Web Server document root with Apache running as root… This shit still happens nowadays.
Before starting the enumeration phase on SMB we need to know one thing previously, what is the Operating System running on the remote machine?
Enumerating SMB Running on Linux
There exist many tools on the Internet to scan and attack SMB, here I will explain the most common ones like smbmap, smbclient, crackmapexec, and enum4linux. For this example, I use the metasploitable2 machine.
Let’s start scanning our remote machine and try to root it!
nmap 192.168.1.91
After scanning our machine we can validate that ports 139 e 445 are open and running SMB with Netbios integration capabilities.
The next step is to verify if exists any shared folder and what permissions they have.
Read the Full SMBMap Guide
Public Shares
Public shares are directories or folders on a system that are made accessible to network users without requiring specific credentials.
smbmap -H 192.168.1.91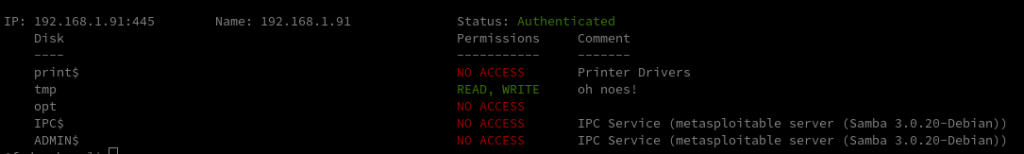
As we can see we have five shares available and only one of them has Read & Write permissions but at this point we don’t know any usernames or passwords, what can we do? Investigate the /tmp folder using another parameter.
List Remote Share
smbmap -H 192.168.1.91 -R tmp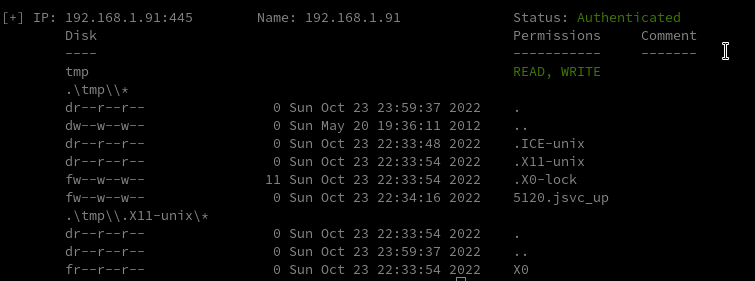
SMB Null Sessions
SMB Null Sessions refer to a type of interaction with the Server Message Block (SMB) protocol where a user establishes a connection to a network resource without providing any credentials.
Null sessions were traditionally used for various administrative and diagnostic purposes, but they also posed significant security risks.
By default, smbmap tests the null sessions but if you need it here it is the command:
smbmap -H 192.168.1.91 -u "" -p "" -R tmpnmblookup -A <IP>Enumerating SMB on Windows
Enumerating SMB (Server Message Block) on Windows systems is a common task during penetration testing, security assessments, or troubleshooting.
It involves gathering information about SMB shares, users, and other related details.
SMB Share Enumeration
Use the net share command to list shared resources on a Windows system. This provides information about available shares.
User Enumeration
Execute the net user command to list user accounts on the target system. This can help identify potential usernames.
SMB Version Detection
Use the smbclient tool with the -L option to list available shares. For example, smbclient -L //[target_IP] provides a list of accessible shares.
SMBClient for Anonymous Access
Attempt anonymous login using the smbclient tool.
For example, smbclient -L //[target_IP] -U% attempts to connect with an empty username and password.
Null Session Enumeration
Tools like enum4linux or smbmap can be used to enumerate information from null sessions. For example, enum4linux -a [target_IP] or smbmap -H [target_IP] can provide details about users and shares.
SMBSigning Enumeration
Use tools like smbmap and the --unauth option to check if SMB signing is enforced. This may impact the ability to perform certain attacks.
Brute Force Attacks
Brute force attacks can be attempted using tools like Hydra or Medusa to guess passwords for SMB accounts.
SMB Vulnerability Scan
An SMB (Server Message Block) vulnerability scan is a fundamental component of cybersecurity assessments, focusing on identifying weaknesses within the SMB protocol widely used for file and printer sharing in Windows networks.
This scanning process involves systematically probing networked systems to assess the security posture of the SMB service, seeking potential vulnerabilities that could be exploited by malicious actors.
SMB Exploitation
SMB (Server Message Block) exploitation involves the unauthorized use of vulnerabilities or weaknesses within the SMB protocol to gain access, control, or perform malicious activities on a target system.
SMB Relay Attack
An SMB relay attack is a cybersecurity exploit that leverages the Responder toolkit to intercept SMB (Server Message Block) authentication sessions within an organization’s internal network.
The attacker can then relay these intercepted sessions to a targeted machine. If the authentication process is successful, the attacker gains unauthorized access to the targeted system, effectively dropping them into a system shell.
This method allows the attacker to move laterally through the network, potentially compromising sensitive data and systems. More comprehensive details about this attack can be found in the associated resources.
Remote Command Execution on SMB
enum4linux -a -R 500-600,950-1150python smbmap.py -u 'admin' -p 'qwerty1234!' -d ACME -H 10.1.3.30 -x 'net group "Domain Admins" /domain'Metasploit SMB vulnerability scanner
In the world of cybersecurity, the Metasploit SMB vulnerability scanner stands as a powerful tool designed to identify and exploit vulnerabilities in the Microsoft Server Message Block (SMB) protocol.
This comprehensive tool provides users the capability to safeguard their networks by scanning for potential weaknesses, and further, exploiting them under controlled conditions to understand their impacts.
It plays a significant role in penetration testing and network defense strategies, providing an indispensable layer of security in today’s digital landscape.
This article unravels the functionality, relevance, and usage of the Metasploit SMB vulnerability scanner in maintaining robust cybersecurity measures.
Eternal Blue
SMB login via Brute Force
PSexec to connect SMB
Rundll32 One-liner to Exploit SMB
SMB Exploit via NTLM Capture
Samba Symlink Directory Traversal
Detecting Zerologon with CrackMapExec (CVE-2020-1472
CrackMapExec SMB: Hacking Samba service
| Vulnerability | Description |
|---|---|
| EternalBlue (MS17-010) | Exploits a vulnerability in Microsoft Windows SMB protocol. Allows remote code execution without user interaction. Notorious for WannaCry and NotPetya attacks. |
| EternalRomance (MS17-010) | Another exploit from the Shadow Brokers leak targeting the same vulnerability as EternalBlue. Facilitates remote code execution. |
| SMBGhost (CVE-2020-0796) | A wormable vulnerability in SMBv3.1.1, affecting Windows 10 and Windows Server 2019. Allows an attacker to execute code remotely. Microsoft released a patch. |
| SMBLoris (CVE-2020-1206) | An SMBv3 server memory corruption vulnerability that allows an attacker to execute arbitrary code on a target system. Patched by Microsoft. |
| Badlock (MS16-047) | Another exploit from the Shadow Brokers leak targeted the same vulnerability as EternalBlue. Facilitates remote code execution. |
| MS08-067 | A critical vulnerability in the Server service of Windows that could allow remote code execution. Exploited by the Conficker worm. |
| MS09-001 | Vulnerability in the SMB protocol that could allow remote code execution. Affected Windows 2000, XP, and Server 2003. |
| MS09-050 | Addresses vulnerabilities in SMBv2 that could allow remote code execution on affected systems. |
| MS09-063 | A vulnerability in the Server service of Windows that could allow remote code execution. Affected various Windows versions. |
| MS10-020 | Vulnerabilities in the SMB protocol that could allow remote code execution on affected systems. |
| MS11-080 | A security update to address vulnerabilities in SMB client that could allow remote code execution. Affected various Windows versions. |
| MS17-010 | A vulnerability in the Microsoft Windows Security Account Manager (SAM) and Local Security Authority (LSA) remote protocol. This could lead to man-in-the-middle attacks. |
| MS17-012 | A security update to address vulnerabilities in SMB clients that could allow remote code execution. Affected various Windows versions. |
| MS17-33 | Addresses a vulnerability in the SMBv1 server. |
| MS19-029 | A security update to address a vulnerability in Windows SMBv3.0 protocol. Allows remote code execution. |
| MS19-076 | Resolves a vulnerability in the Windows SMB server that could allow remote code execution. |
| MS21-071 | Addresses a security vulnerability in the Microsoft Server Message Block 3.1.1 (SMBv3.1.1) protocol. Allows remote code execution. |
SMB Exploits – Linux
In Linux, the SMB protocol is implemented using the Samba software suite, which provides file and printer-sharing services to Windows clients.
- EternalBlue: EternalBlue is a remote code execution exploit that targets a vulnerability in the SMBv1 protocol. It was used in the WannaCry ransomware attack in 2017 and can also be used to target Linux systems running Samba.
- SambaCry: SambaCry is a remote code execution exploit that targets a vulnerability in the Samba software suite. It was discovered in 2017 and can be used to target Linux systems running Samba versions 3.5.0 to 4.6.4.
- SMBLoris: SMBLoris is a denial-of-service (DoS) exploit that targets a vulnerability in the SMB protocol. It can be used to overload the SMB service on a target system, causing it to crash or become unresponsive.
- MS17-010: MS17-010 is a vulnerability in the SMBv1 protocol that allows for remote code execution. It was exploited by the WannaCry ransomware and can also be used to target Linux systems running Samba.
It is important for Linux system administrators to keep their systems up to date with the latest security patches and to configure their systems securely to prevent SMB exploits.
This includes disabling SMBv1 and ensuring that Samba is configured securely with proper access controls and authentication mechanisms.
Additionally, network administrators can use intrusion detection systems to monitor for attempts to exploit SMB vulnerabilities and block them in real-time.
SMB Exploits – Windows
- EternalBlue: EternalBlue is a remote code execution exploit that targets a vulnerability in the SMBv1 protocol. It was used in the WannaCry ransomware attack in 2017 and can also be used to target Windows systems.
- MS08-067: MS08-067 is a vulnerability in the Server service in Microsoft Windows that allows remote code execution when the service is running. The vulnerability was discovered in October 2008 and was addressed by Microsoft with a security patch shortly thereafter.
- MS17-010: MS17-010 is a vulnerability in the SMBv1 protocol that allows for remote code execution. It was exploited by the WannaCry ransomware and can be used to target Windows systems.
- SMBGhost: SMBGhost is a remote code execution exploit that targets a vulnerability in the SMBv3 protocol. It was discovered in March 2020 and can be used to target Windows systems running SMBv3.
- ms08_067_netapi
- Eternal Blue
- SMB login via Brute Force
- PSexec to connect SMB
- Rundll32 One-liner to Exploit SMB
- SMB Exploit via NTLM Capture
It is important for Windows system administrators to keep their systems up to date with the latest security patches and to configure their systems securely to prevent SMB exploits.
This includes disabling SMBv1 and ensuring that SMBv2 and SMBv3 are configured securely with proper access controls and authentication mechanisms.
Additionally, network administrators can use intrusion detection systems to monitor for attempts to exploit SMB vulnerabilities and block them in real-time.
SMB Post Exploitation
Post-exploitation techniques on systems running the Server Message Block (SMB) protocol involve actions taken by an attacker after gaining unauthorized access.
Lateral Movement
Pass-the-Hash (PtH): Exploiting cached password hashes to move laterally within the network without knowing the plaintext passwords.
Exploiting Vulnerabilities: Identifying and exploiting vulnerabilities in the target system to escalate privileges and gain higher-level access.
Creating User Accounts: Creating new user accounts with elevated privileges to ensure continued access.
Trojan Horses: Deploying Trojan horse malware to perform additional malicious activities.
SMB TRAP
SMB-Trap is a technique that takes advantage of the automatic authentication behavior of the Windows library URLMon.dll.
When a web page attempts to access content using the Server Message Block (SMB) protocol, such as images hosted on a remote server, the Windows library URLMon.dll will automatically try to authenticate to the host.
This behavior occurs with functions like URLDownloadToFile, URLDownloadToCache, URLOpenStream, and URLOpenBlockingStream, which are commonly used by browsers and tools like Skype.
By exploiting this automatic authentication process, attackers can set up a malicious trap that tricks the system into unintentionally disclosing authentication credentials or establishing connections with unauthorized servers.
This presents a significant security risk, as it can lead to unauthorized access or data leakage on the affected system.
wmiexec and dcomexec
The purpose of using wmiexec and dcomexec is to stealthily execute a command shell without leaving traces on the disk or initiating a new service, leveraging DCOM via port 135 for communication. These tools provide attackers with a means to remotely access and control systems by bypassing traditional security mechanisms and maintaining a low profile during unauthorized access.
Wmiexec and dcomexec can be utilized surreptitiously due to their ability to operate without creating new files on the target system or triggering antivirus software alerts. By using these tools, an attacker can interact with a compromised system discreetly, avoiding detection by security measures that typically monitor file activity or service creation.
Furthermore, wmiexec and dcomexec allow for the execution of commands or scripts remotely, enabling attackers to perform malicious activities without directly interacting with the target machine. This capability facilitates a stealthier approach to manipulating systems and exfiltrating data without raising suspicion.
Overall, wmiexec and dcomexec serve as powerful tools for executing commands on target systems covertly, providing attackers with the means to maintain access and control without alerting security protocols.


Comments